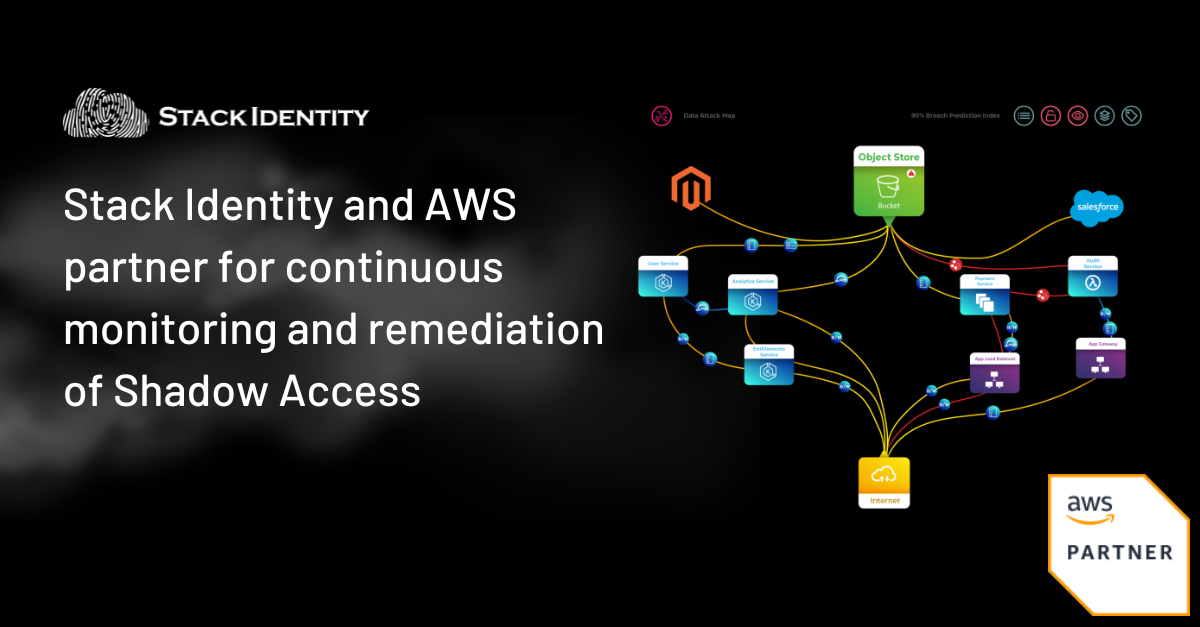
Through its live data attack map and patent-pending breach prediction index (BPI) the Stack Identity platform enables AWS customers with the following capabilities:
- Continuous monitoring and remediation of Shadow Access for multi cloud environments
- Detection of the 2% of toxic combinations that impact 90% of data assets
- Ability to implement a risk-driven cloud security posture
- Prevent data exfiltration and ransomware attacks
- Enforce automated Identity Governance
Why Identity and Access is the Lynchpin to Securing Cloud Data
Identity and access exposures in the cloud is a large, pernicious issue that can take diligence to even realize you have. It culminates in a problem of “Shadow Access” – unauthorized, unmonitored and invisible access that needs to be addressed and removed before it can be weaponized by attackers. Shadow Access results in toxic combinations of identities and permissions that can be used to breach cloud environments and exfiltrate data. AWS alone has over 13,000 API connections with 14,000 permissions to access cloud data and services.
Some examples of Shadow Access in Amazon S3 environments include:
| Invisible Access | AWS console did not show effective permissions for an S3 bucket when scanning which led to an S3 bucket being left open |
| Toxic Combination | Programmatic access to an S3 Bucket via an application identity along with permission management permissions |
| Data Recovery Access | Assumed role access to programmatic access to an S3 bucket used for data backup for Data Recovery |
Impact of Shadow Access in Data Breach of LastPass S3 Bucket
AWS customers are often unaware of the invisible risks of Shadow Access. For example, the LastPass data breach was primarily caused by disjointed IAM and cloud operations.
On Aug 8, 2022, in the first identity and access incident in the LastPass data breach the attacker gained access to an S3 bucket containing a) a source code folder and b) an encrypted backup folder of LastPass customer data. The attacker was able to do this by leveraging permissions which were never used before by an over-permissioned identity giving it overly-scoped access to folders, including the backup folder of LastPass customer data.
In the second identity and access incident on Oct 26, 2022, the attacker managed to target one of the 4 DevOps engineers’ identities and installed a keylogger that captured the master key and then proceeded to exfiltrate all the keys inside the secret vault.
Learn more about how the LastPass data breach of an S3 bucket was actually caused by Shadow Access in this blog.
Unintended Disclosure of IAM Access Keys – The Most Common Event That Leads to Ransomware in AWS
With Stack Identity, AWS customers can directly take action against ransomware attacks in S3. The AWS Customer Incident Response Team (CIRT) calls out that unintended disclosure of Identity and Access Management (IAM) access keys is the most common event that leads to a ransomware event that targets data in Amazon S3.
The recommended solution from the AWS CIRT team to address this problem is DIY – using several products – Cloudtrail for activity logs, Cloudwatch metrics for abnormal transfer spikes, GuardDuty for anomalous API activity and various ancillary log services to pick up additional context. This is just for Amazon S3 and unfeasible to do at scale, across multi-cloud environments.
Learn more about Stack Identity and how it helps prevent ransomware in AWS by protecting unintended disclosure of IAM access keys in this blog.
Summary
AWS customers using Stack Identity gain continuous visibility, automated right sizing of permission drift and just-in-time governance, and security and data owners can quickly prioritize impact and authorize remediation before it turns into a “security incident”.
- Read the Stack Identity and AWS datasheet
- Learn more about the Stack Identity platform here
- Schedule a demo here
- Access Stack Identity on AWS Marketplace here.
