Explosive data sharing in the Cloud and AI era proliferates identities and entitlements resulting in Shadow Access risks
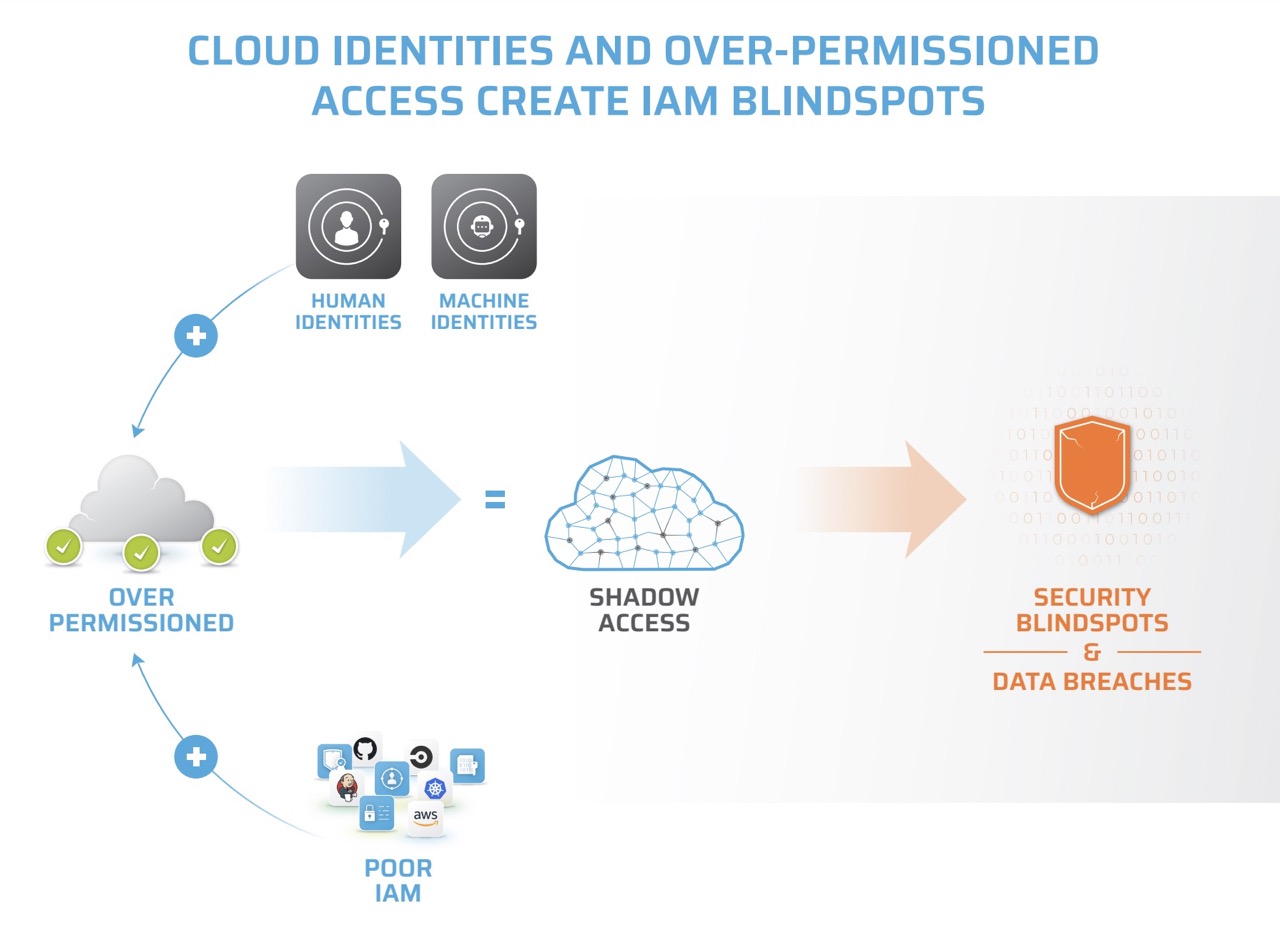
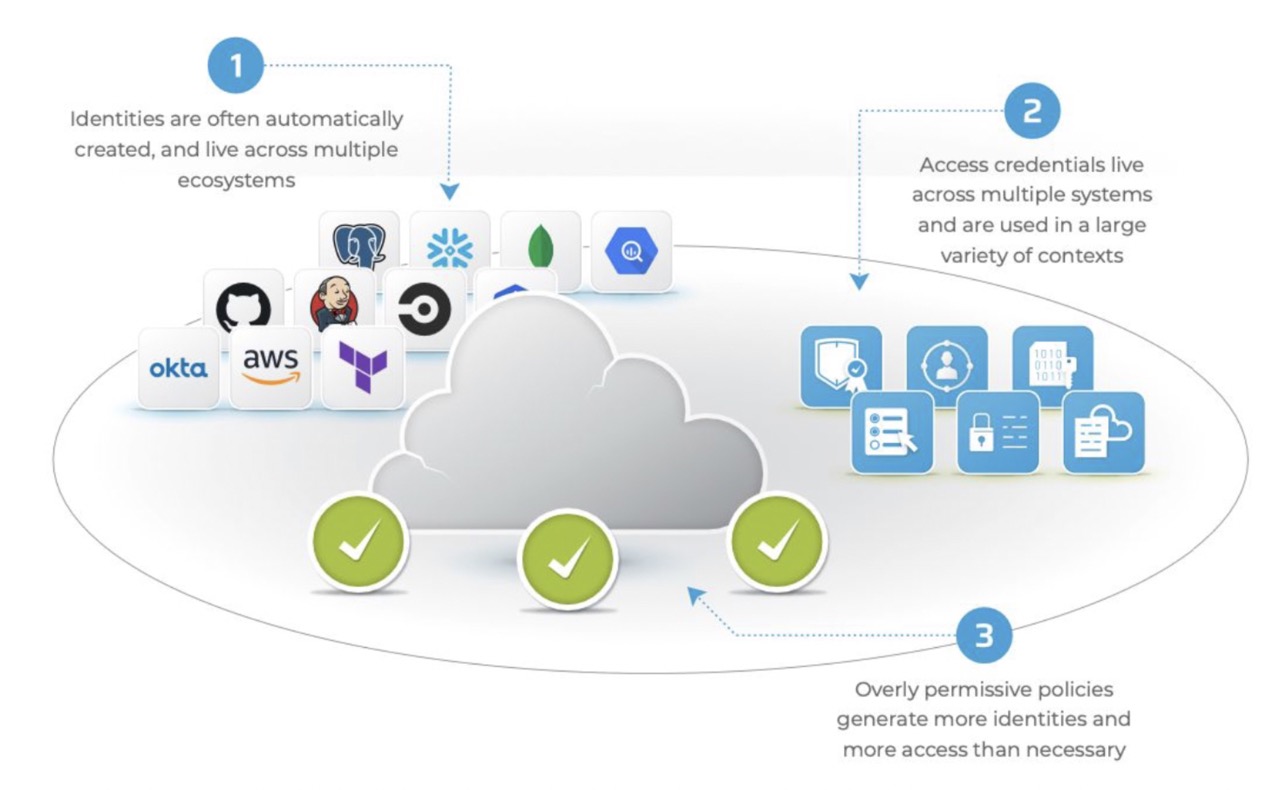
Automated Infrastructure as Code (IaC) processes create an explosion of over-privileged access and entitlements. At the same time, zettabytes of data are being shared with cloud apps, services, third parties, and AI. The intersection of these two trends has given rise to a new concern: Shadow Access.
Shadow Access is unauthorized, unmonitored, unintended and invisible access to sensitive data, applications and software and leads to data breaches, compliance violations, operational disruptions, and security vulnerabilities.
Addressing Shadow Access demands transforming
Cloud IAM to secure the Cloud
However, unlike software vulnerabilities, malware, or new ransomware, identity is a security vector where enterprises can have complete control and accurately answer questions of:
- Who has access to what?
- Who is actively using these permissions?
- Are they authorized for such access?
- What unauthorized activities are happening beneath the surface?
Stack Identity’s unified platform continuously detects and eliminates Shadow Access before an attacker can exploit it
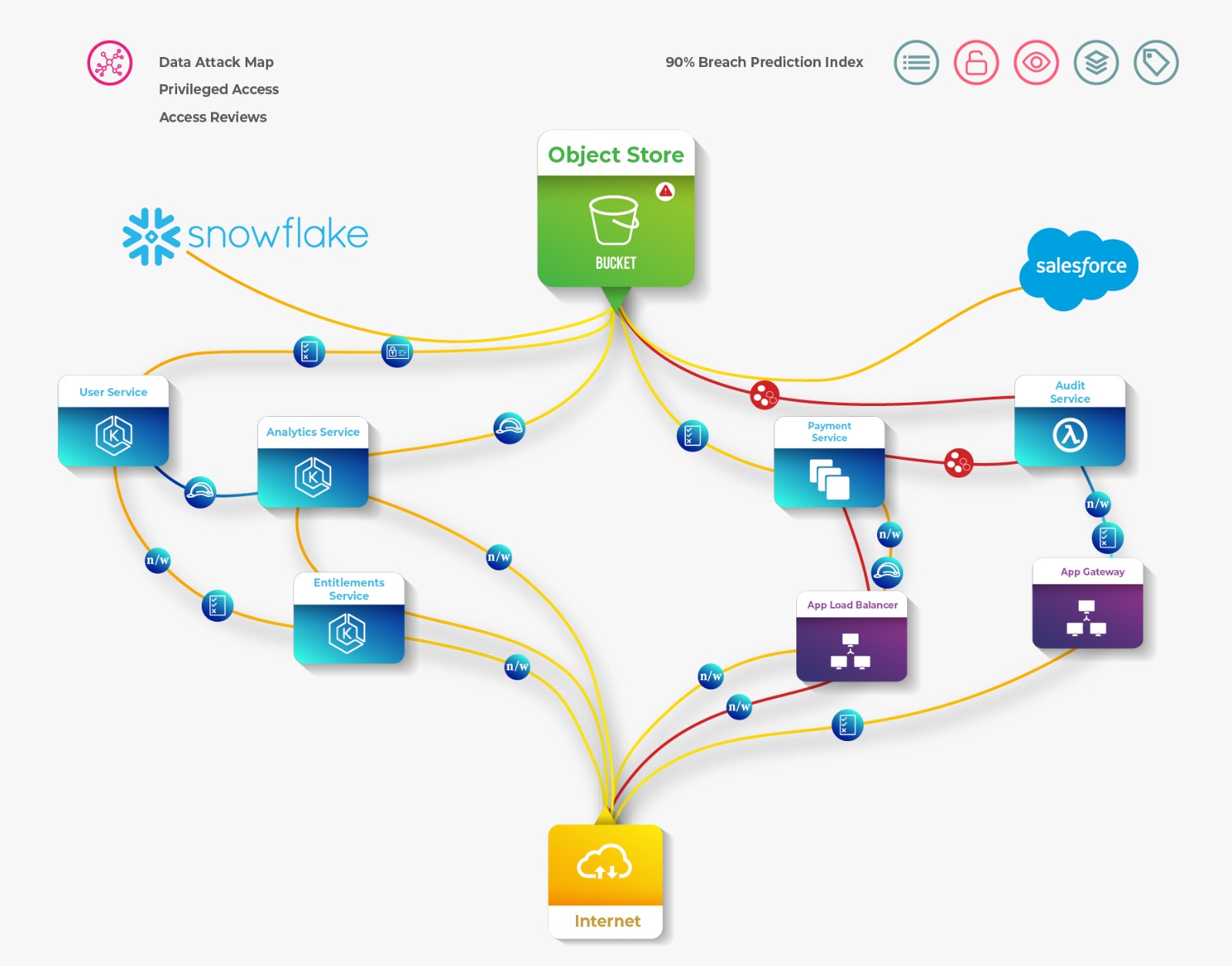
We empower Cloud SecOps, DevOps and Compliance teams with an integrated approach to CIEM, ITDR and Cloud IGA with the comprehensive visibility needed to assess, review, remediate, and refine their cloud identity and access controls.
Leadership Team

Venkat Raghavan
FOUNDER & CEO

Ambrish Deshpande
CO-FOUNDER | SALES & BD

Sanjay Kale
CO-FOUNDER | R&D | CISO

Amol Patil
HEAD OF ENGINEERING
