Shrink Attack Surface
Reduce Privilege Exposure
Gain Immediate ROI

What’s New?
Products
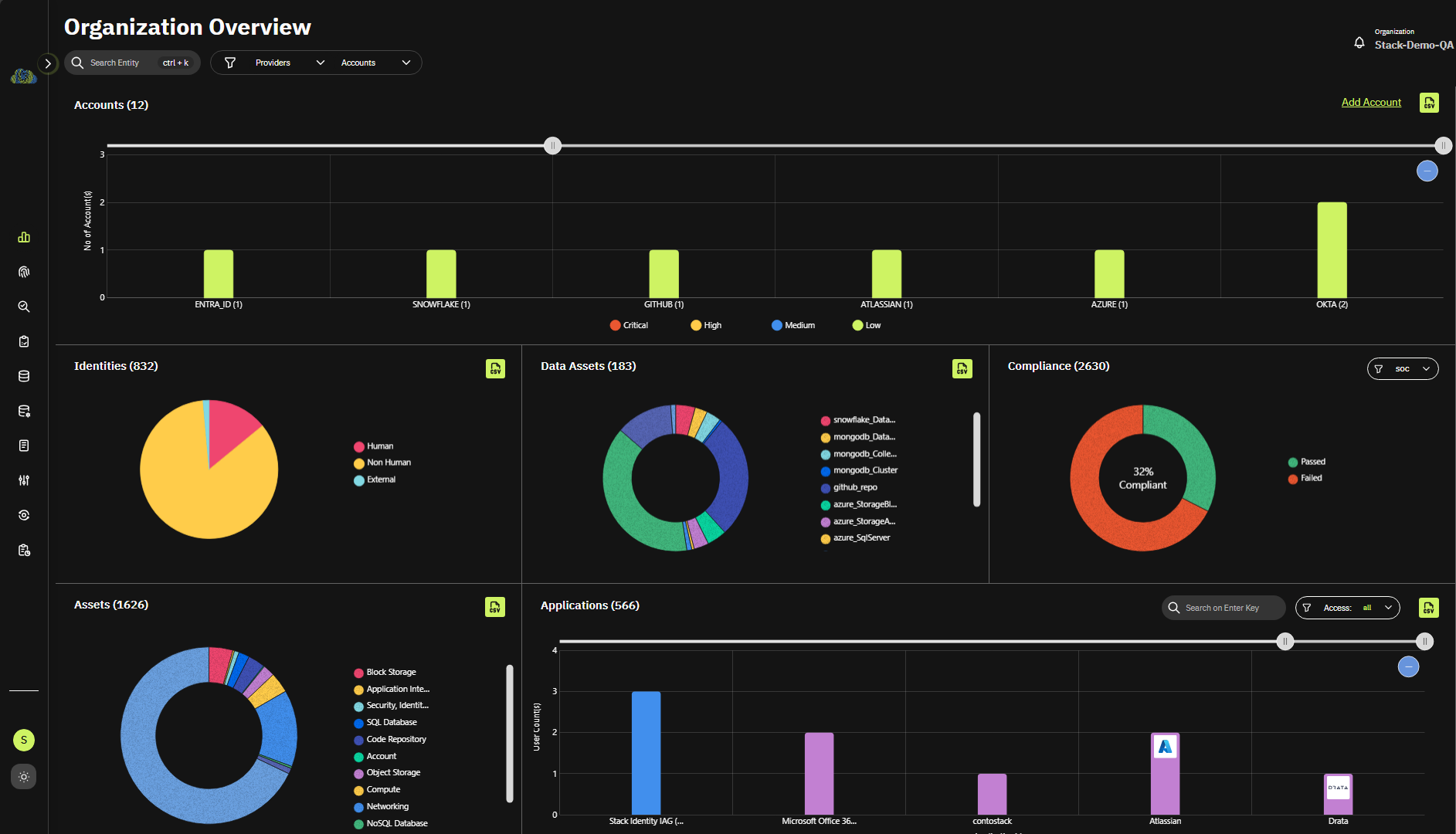
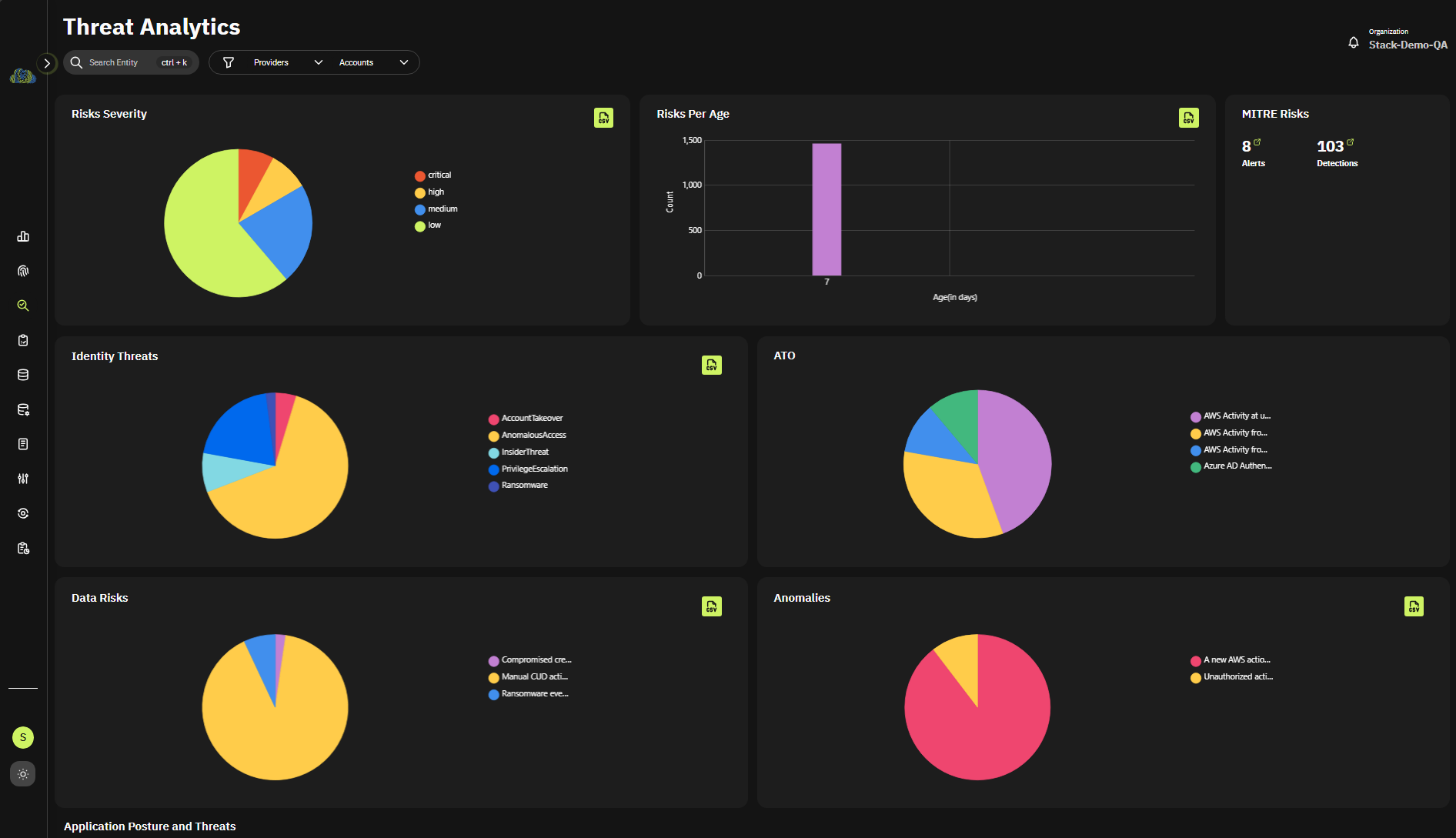
CIEM
ITDR
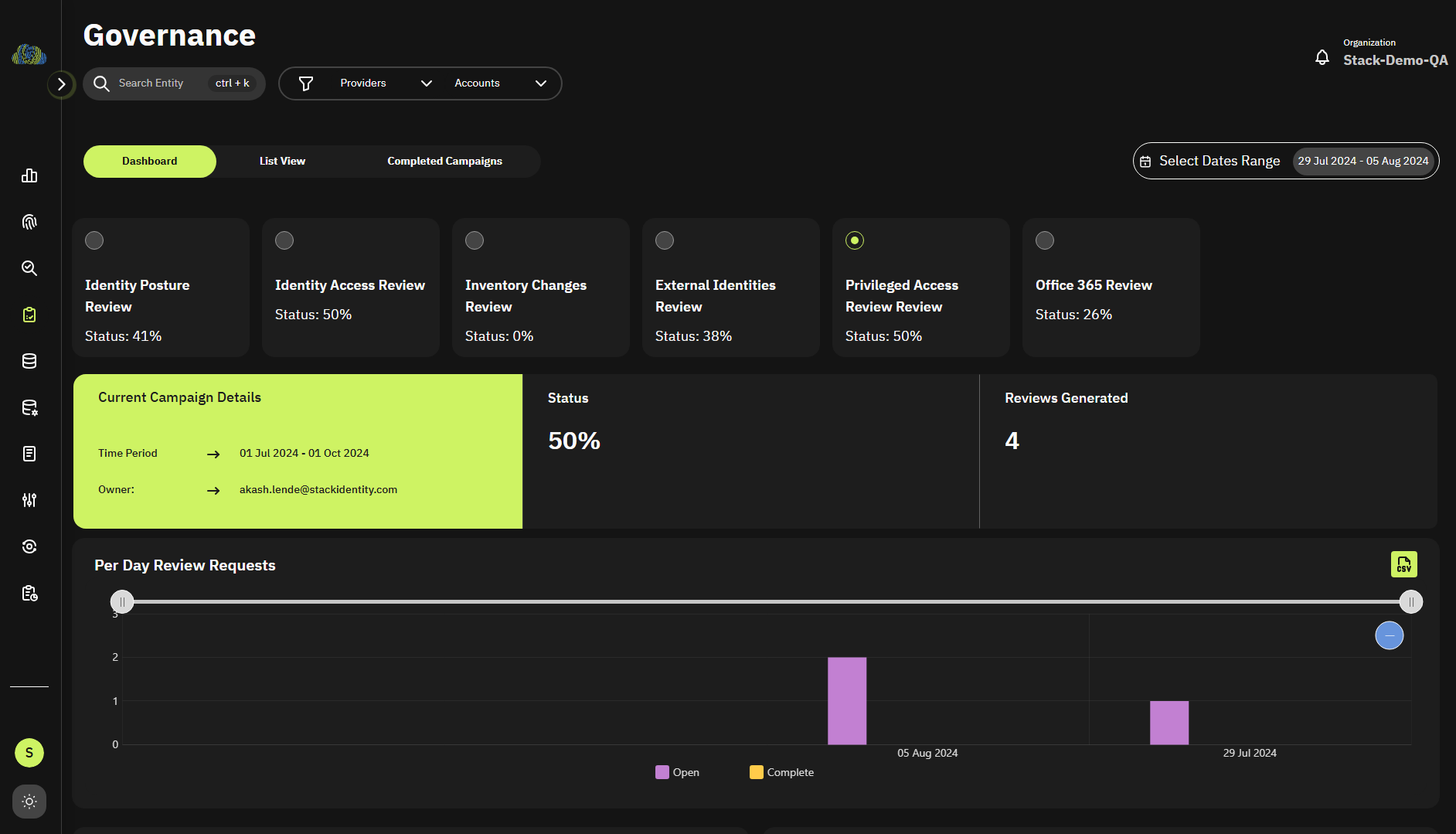
Realtime IGA
Cloud Infrastructure Entitlement Management (CIEM)
- Connected context
- Visibility and monitoring
- Automated detections
- Rightsize your cloud policies
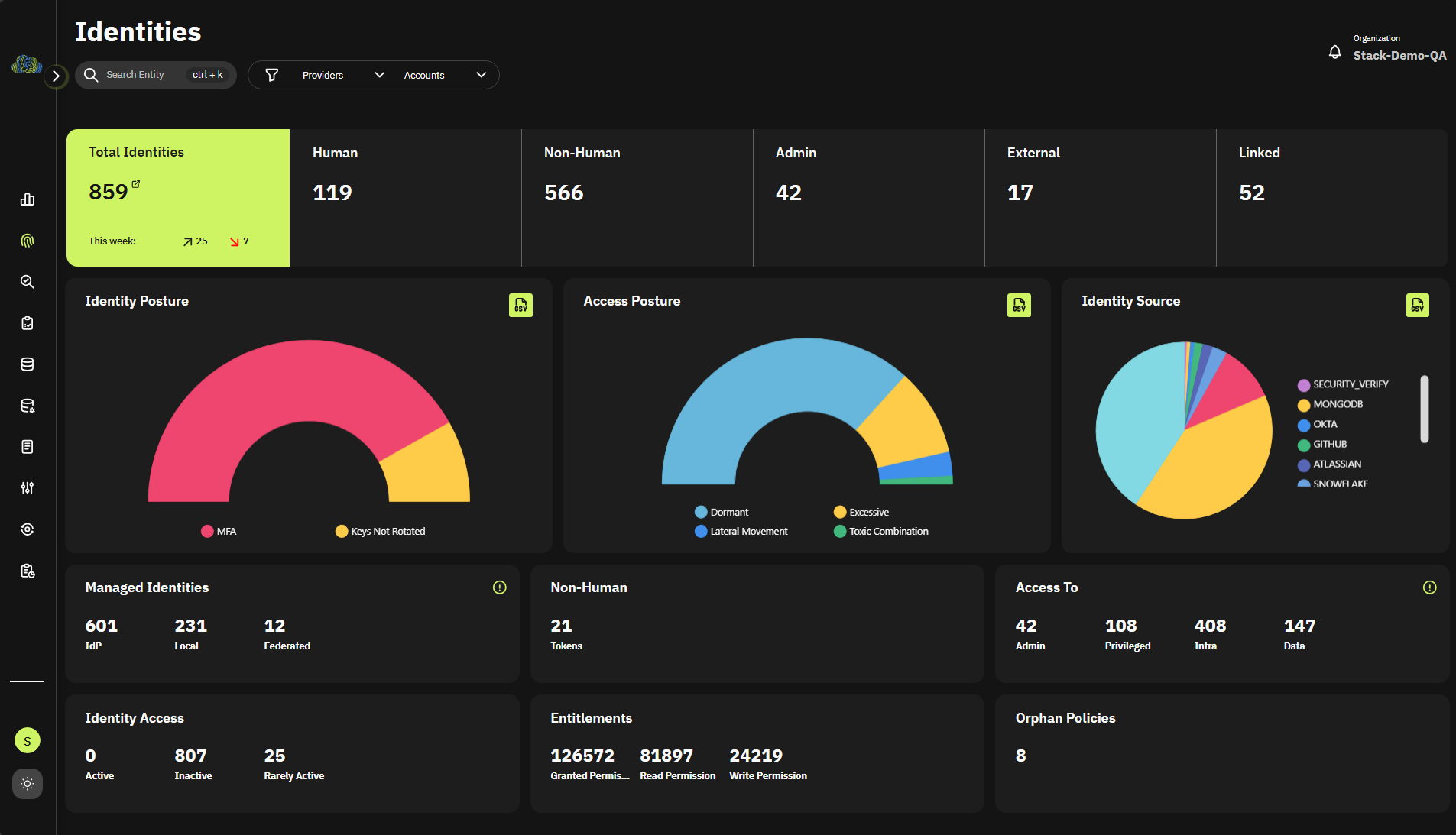
Identity Threat Detection and Response (ITDR)
- Reveal Identity Risks
- Determine Threats
- Remediate with Workflows
Cloud Identity Governance and Administration
- Connected context
- Instant access reviews
- High-value data access reviews
- Right-size policies
Testimonials
“The biggest risk to protecting cloud platforms, including AWS, is securing who has access to it, and in an overly-permissioned environment with multiple identities involved, data exfiltration can occur through multiple shadow access pathways. Continuous visibility with rich context is essential to empower security and engineering teams to audit, govern, and promptly rightsize access.”
Sean Ventura
Head of Security & Compliance, KinderCare
“The status quo of overly permissioned cloud accounts with long-standing privileges and static entitlements creates an environment where Shadow Access thrives. The Shadow Access research report brings a data-driven baseline to identify gaps in IAM governance and how best to rethink the governance process to effectively work in automated cloud-native environments.”
Ken Foster
“Our AWS cloud ecosystem is a mix of automated DevOps and manually managed infrastructure. “Stack Identity gives continuous visibility into our data exposure risks with the ability to automate least privileged enforcement for both our security and engineering operations teams.””
Steve De Jong
Distinguished Engineer, Vercara
Excessive Access:
An identity would be given some permissions initially, but it might use only a subset of the attached permissions.
• Full admin permissions are given to an identity, but it only does management operations on specific resources
• Read/write access given to an identity, but it only uses read access
Unsafe Access:
• MFA not enabled for a user with admin permission
• Login/access attempts from an IP blacklist
• A role being assumed from a compute which is directly exposed to the internet or running a vulnerable software
• An administrator with tons of powerful access (wide scope of resources)
• A password not rotated in last
Unused Access:
An identity would be given some permissions initially, but it might not be using all those permissions.
• Full admin permissions given to an identity, but it never carries out any management operations
Invisible Access:
An identity can assume a role and thus obtain different sets of permissions to resources in an environment.
• An identity can log in to a compute and run an application that can assume a role that has different permission attached to it
Privileged Access:
Privileged Access is a term used to designate special access or abilities above and beyond that of a standard user. Privileged Access can be associated with human users as well as non-human users such as applications and machine identities.
• An identity that has admin permissions or management permissions
• An identity is authorized to assume a role that has higher privileges/permissions associated with it
• An identity with read access to a resource can assume a role that gives it read/write access to that resource
• An identity with no access to a resource can a assume role that gives it read/write access to that resource


