Is my Cloud Pwned?
What’s the definition of being Pwned?
It’s a Slang. It’s derived from “Owned” and sounds like Powned
It means “To totally defeat or dominate, especially in a video or computer game”
The proliferation of cloud-based infrastructures has revolutionized the way organizations operate, offering unparalleled scalability, accessibility, and flexibility. However, alongside these benefits, the ever-evolving threat landscape presents a pressing challenge: the identification and prevention of anomalous lateral movement within cloud environments.
Attackers now a days are looking for ways to own a cloud infrastructure so that they can conduct various malicious activities ranging from hosting malware sites, crypto mining, data exfiltration etc. They want to fly below the radar and continue the parasitic relationship with the business owners operating in public clouds.
The attackers know that if they create any suspicious activity, they may be caught and stopped, but imagine a situation where there are “No Red Flags” and everything seems to be normal and they continue their malicious intent. Most of the time businesses don’t realize that their public cloud infrastructure is compromised by using shadow access to their own environment and they continue to pay for it.
This is where every business needs to continuously monitor if they are been Pwned or can be Pwned so as to take corrective actions to fix it.
How it works
1. Lateral Movement
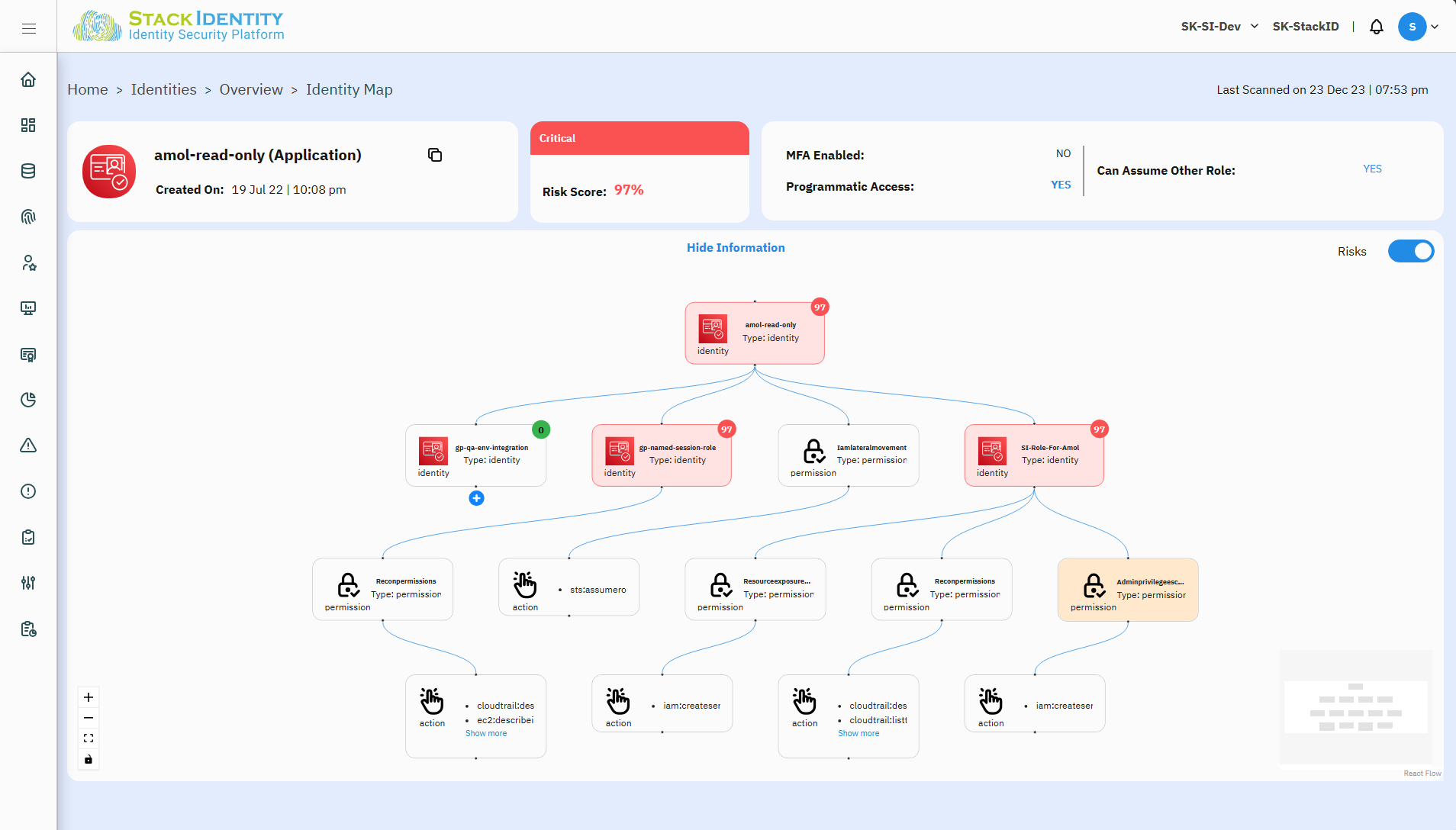
Lateral movement within a cloud environment often involves leveraging machine identities to gain authenticated and authorized access, allowing attackers to move stealthily across the network, potentially escalate privileges without raising suspicion and access critical assets with malicious intent.
Lateral movement orchestrated through compromised machine identities often goes unnoticed as the attackers operate within the confines of authenticated and authorized access. Traditional security measures might fail to detect these movements since the attackers are using legitimate credentials, making it difficult to distinguish their activities from normal system operations. They also fail to provide real-time detection and response capabilities needed to thwart these lateral movement attempts effectively.
2. Excessive Entitlements
Over permissive access for identities, especially machine identities, is the major reason behind lateral movement by attackers. Most cloud environments are over permissioned because developer’s tradeoff deployment velocity for security. Every day the cloud becomes more riskier as development and operations teams are adding new projects, connecting cloud services, adding entitlements, and granting permissions with very little oversight. Configuration mistakes, cut-and-paste roles and permissions, temporary access, exception-based access and band-aids all exacerbate this problem.
The result is that hundreds of thousands of legitimate entitlements and identities in the cloud create unauthorized access pathways that attackers weaponize to own certain infrastructure or many a times take out cloud accounts and exfiltrate data. Removing unauthorized access to prevent account takeovers is a preventable problem with foresight but overburdened operations teams don’t have the time or resources to fix this. Therefore, access vulnerabilities accumulate risk that unfortunately result in incidents or breaches eroding customer trust, inviting regulatory scrutiny and slows down growth initiatives.
The critical challenge lies in developing a robust, proactive system capable of identifying possibility of lateral movements and early signs of it within cloud infrastructures. Addressing this challenge is imperative to ensure the integrity, confidentiality and availability of sensitive data and services hosted in cloud environments.
Stack Identity help our customers to manage Cloud Incidents by providing insights of if they are already pwned or can be pwned in future.
Stack Identity CIP (Cloud Incident Preventor) is a simple and easy to use SaaS solution targeted at AWS Cloud environments. CIP continually scans for access vulnerabilities by which your environment can be compromised and blocks unauthorized access pathways and prevents incidents. The CIP provides insights on both provisioned as well as actual access.
1. Vulnerabilities based on Provisioned Access
This functionality involves conducting comprehensive scans and assessments of the cloud environment to identify potential access vulnerabilities. These include configuration checks, privilege escalation risks and credential management for all the identities.
2. Near Real-time to find Anomalous Access Behavior
This functionality involves continuous monitoring of access activities within the cloud environment to detect deviations from normal or expected patterns. It requires behavioral analysis of identities establishing a baseline access pattern. Any deviation from the baseline may indicate unauthorized access attempt or unusual activity.
3. Real-time notifications and alerts
This functionality involves generating notifications and alerts for security teams and cloud administrators as soon as anomaly or potentially malicious activity is detected. These alerts prompt immediate investigation and remediation actions. The CIP provides all the required context to pinpoint the issue and suggestions for remediation action.
The combined approach of proactive vulnerability scanning and real-time access monitoring allows to offer the following benefits,
- Preventive Measures: By identifying access vulnerabilities proactively, customers can take preventive actions such as adjusting permissions or reconfiguring security settings before potential attacks occur, thereby reducing the attack surface.
- Early Detection of Anomalies: Real-time monitoring enables timely detection of abnormal access patterns or suspicious activities, enabling swift responses to potential threats before they escalate into full-scale attacks.
- Timely Notifications and Alerts: Immediate alerts and notifications empower customers to respond promptly to security incidents, enabling them to investigate, contain and mitigate threats in a timely manner, reducing the impact of potential breaches.
