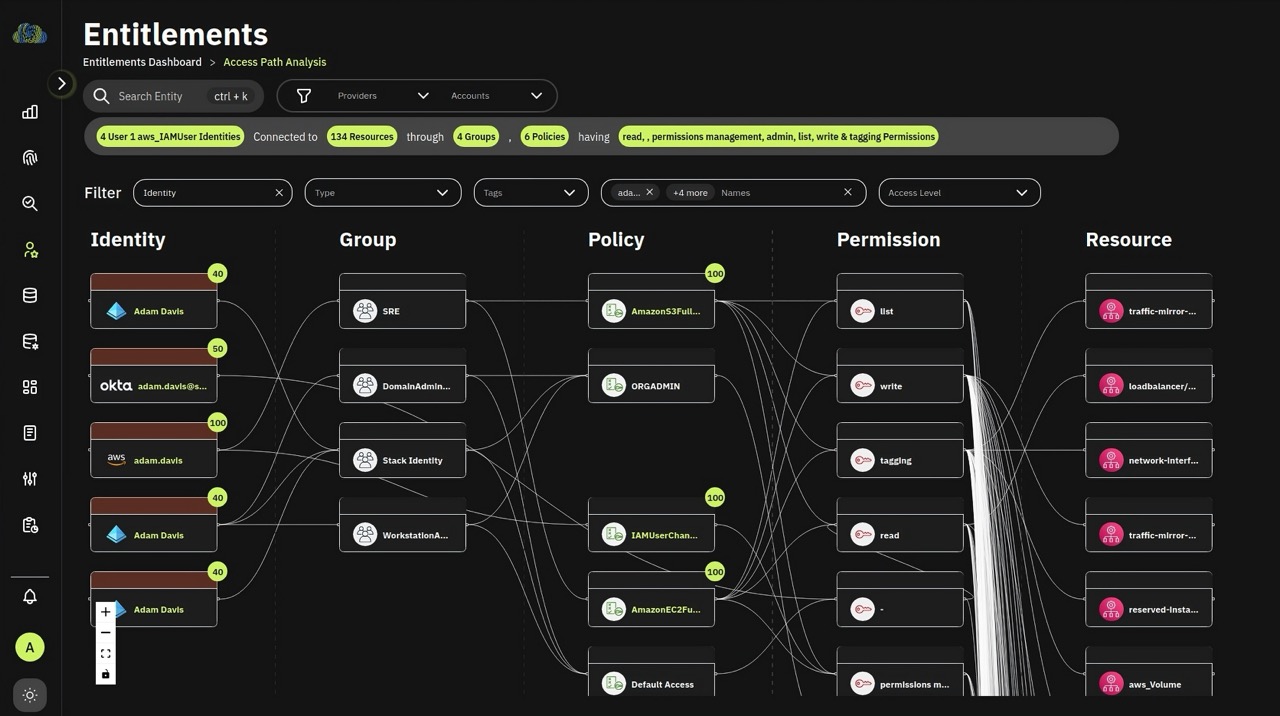
1. Connected context
Identify Cloud IAM exposures by correlating identities (human and non-human), access, entitlements, and governance events across all your cloud systems.
2. Visibility and monitoring
Uncover vulnerable Cloud IAM pathways and lateral movement risks that can be easily weaponized to exfiltrate data.
3. Automated detections
Discover toxic combinations, include change detections, chained access, and overprivileged, unauthorized, and invisible (shadow) access to your crown jewels.
4. Rightsize your cloud policies
To stop permission drift, prevent lateral movement attacks and eliminate Shadow Access to cloud resources.
Extend Further: Extend CIEM to include data security to stop ransomware and breaches and implement just-in-time IAM governance. Take advantage of our open detection platform to develop and share custom detections.
