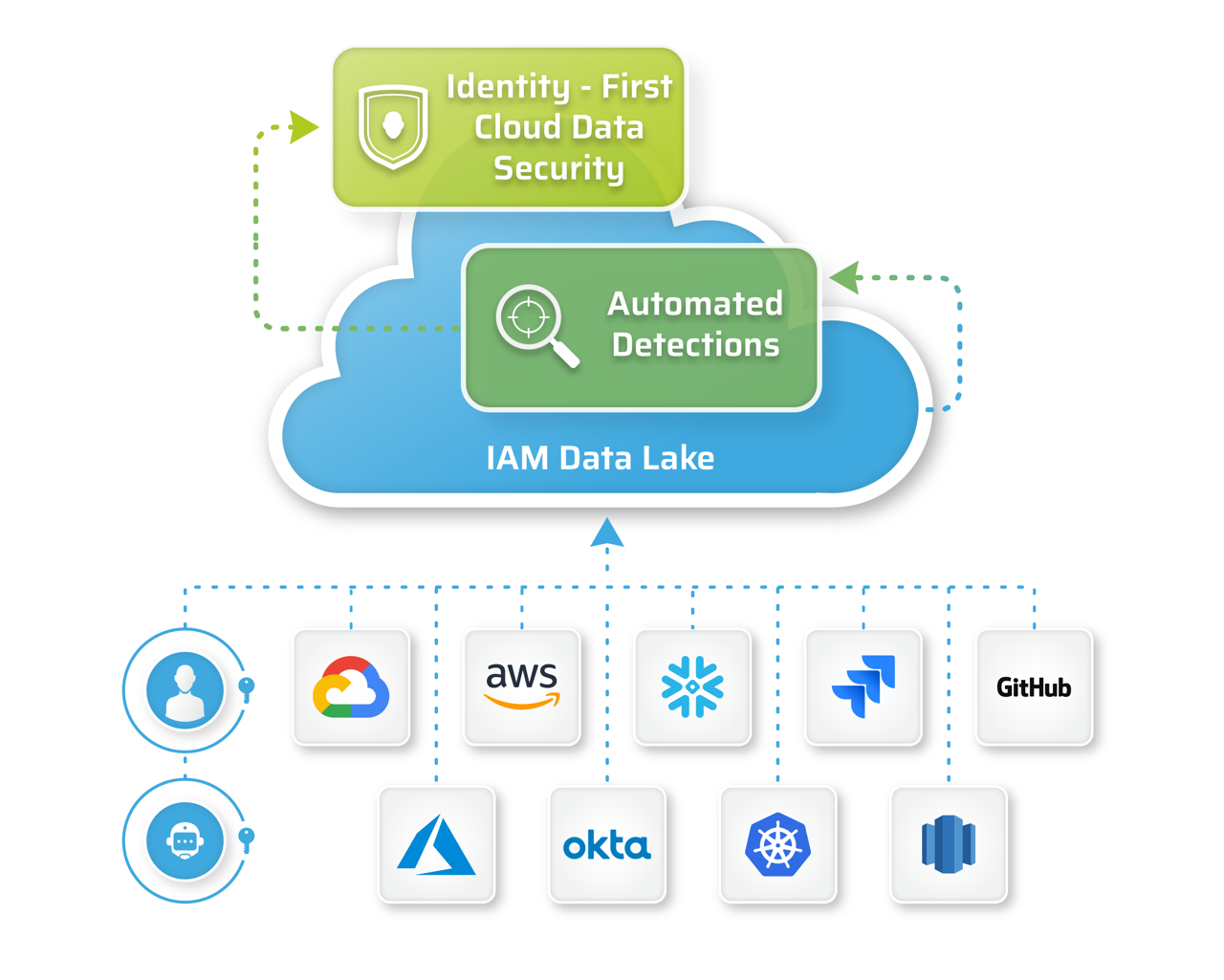
- Unified Platform – Powered by the industry’s first Identity Security Data Lake which consolidates, correlates and contextualizes identity, access risks and vulnerabilities across cloud and data estates.
- Automated detections – Identifies toxic combinations, chained access, lateral movement, drift detection, overprivileged, unauthorized shadow access and shadow identities and policy violations.
- Open API platform – Data enrichment and analytics that enables you to detect, remediate and govern what matters most to your business.
- Extensible platform – Integrates into your multi-cloud environment, IDP systems, ticketing systems, SecOps, IAM and GRC processes.
Extend Further: Take advantage of our open detection platform to develop and share custom detections.
Our platform is built upon an IAM Data Lake to answer the most pressing security questions in your multi cloud environments
with speed and simplicity.
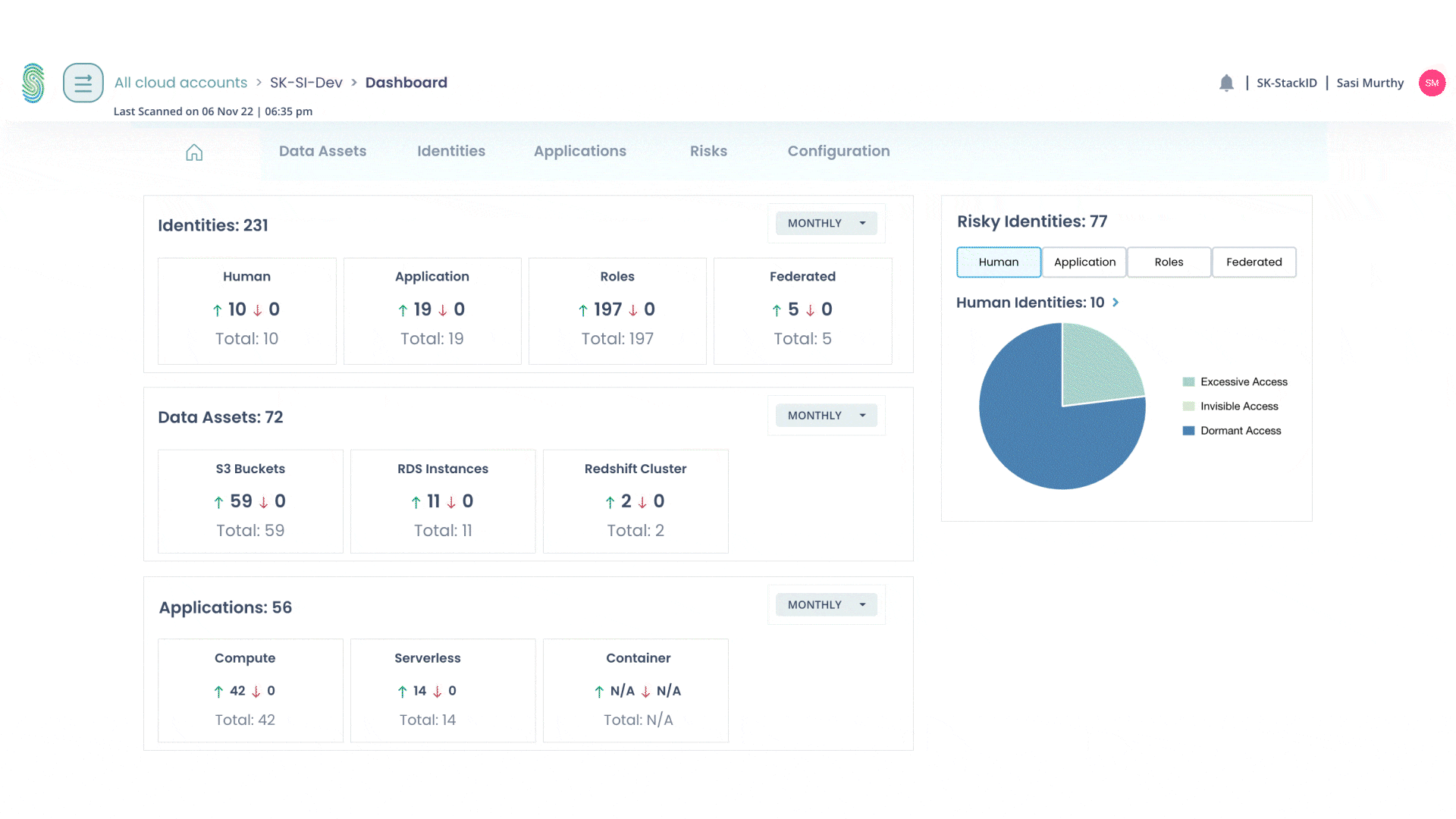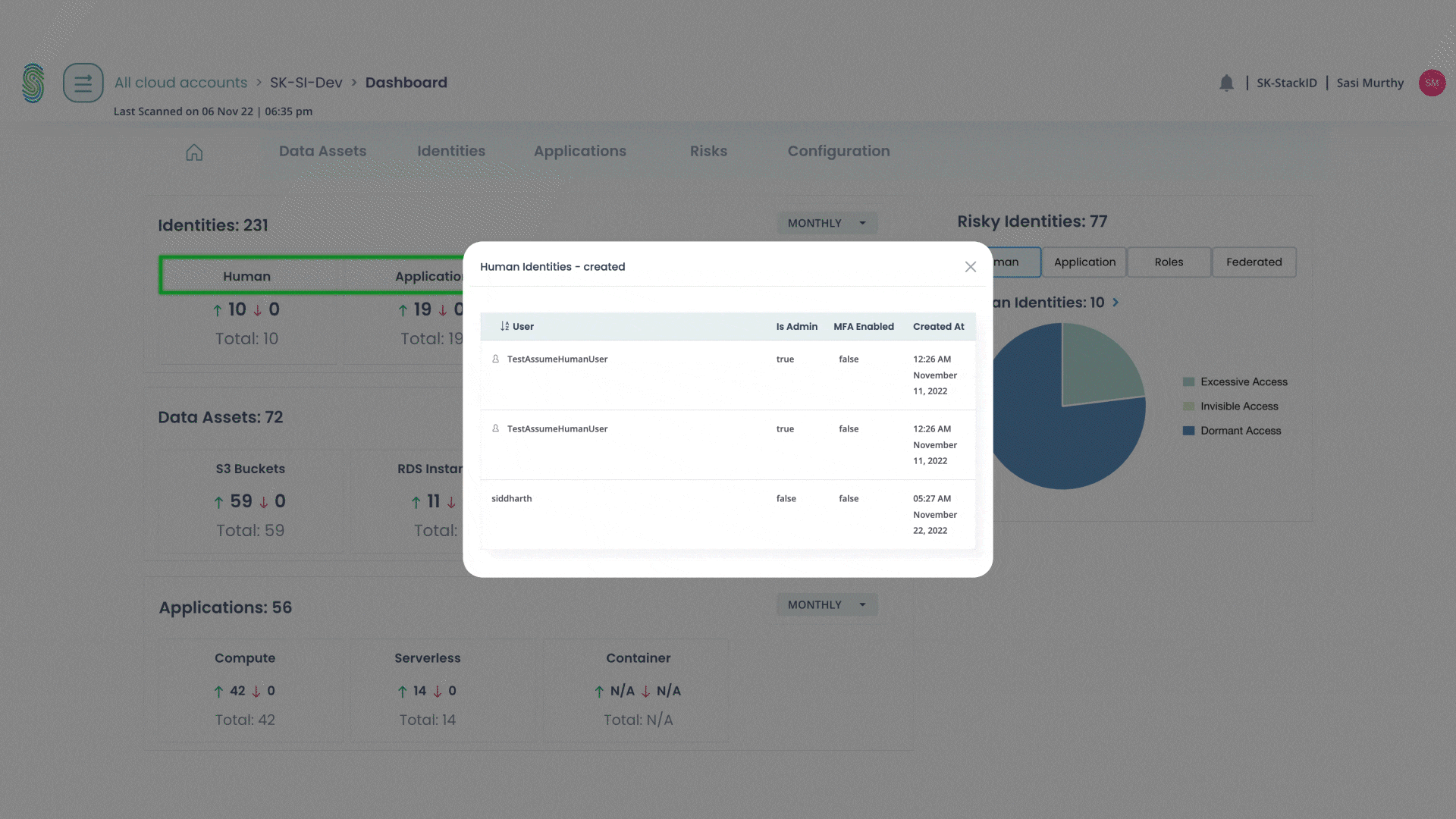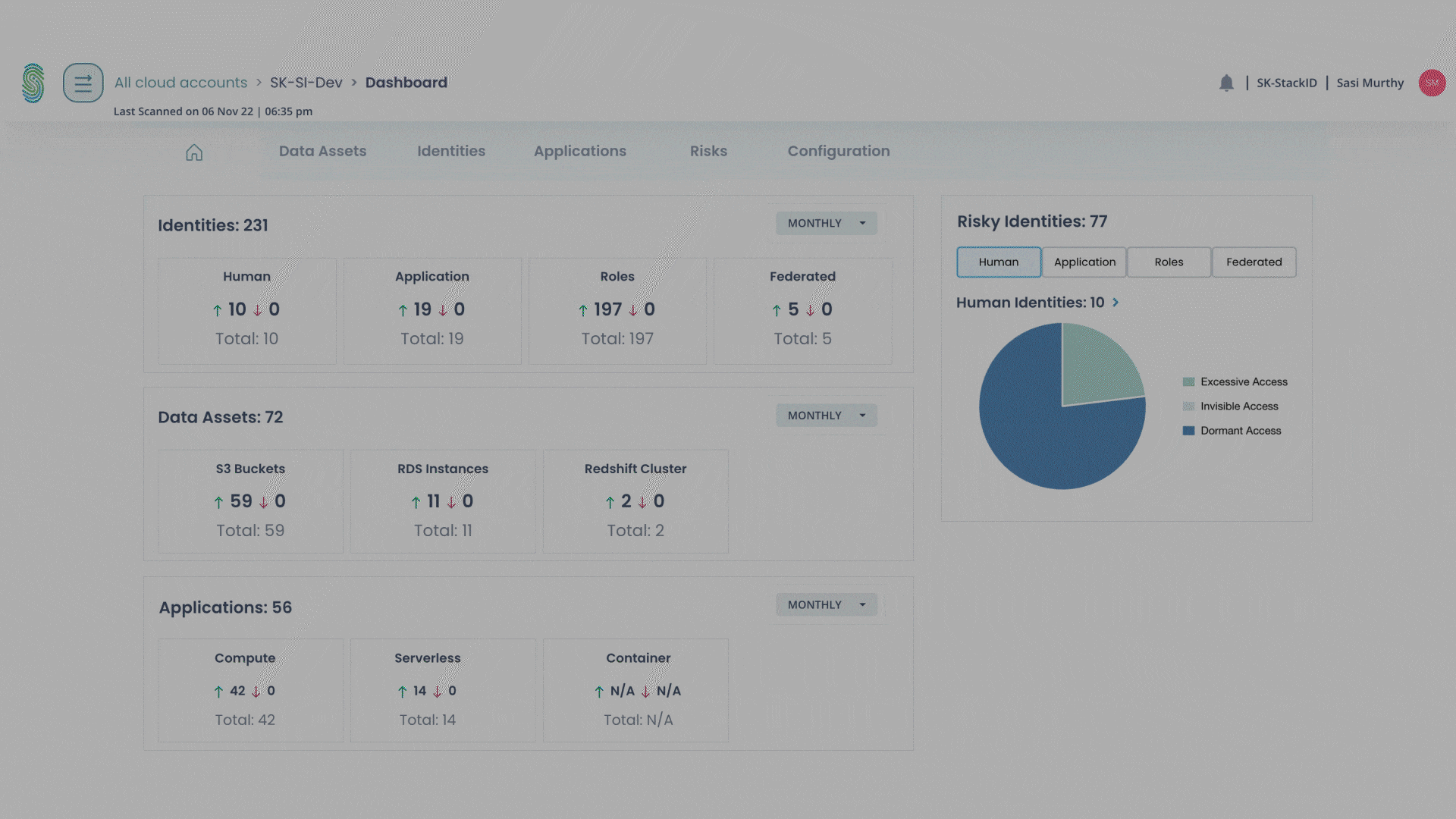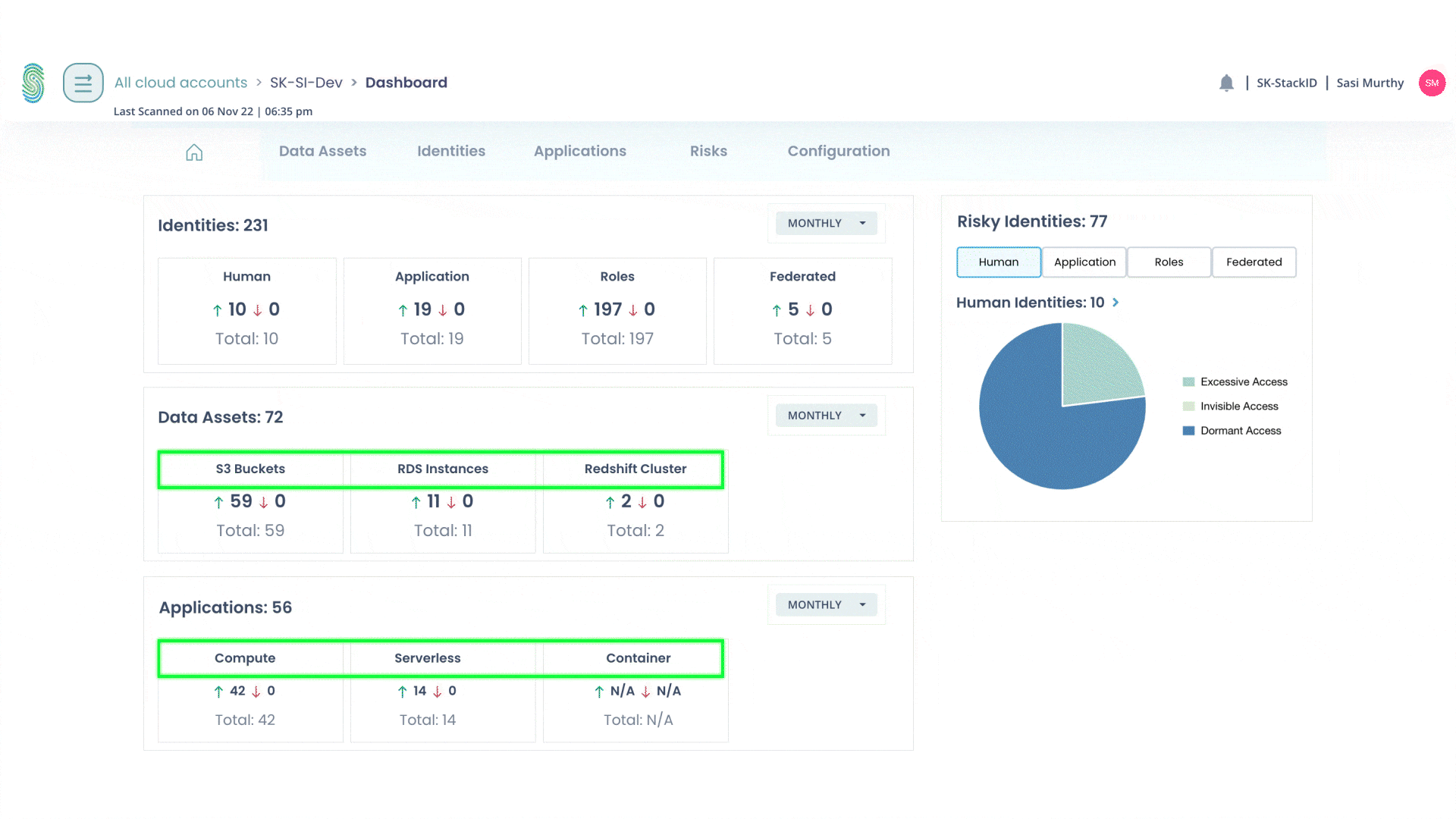
Baseline Your Cloud Inventory
For easy SOC2 and cloud compliance reports
- Find your identities and roles
- Find your data assets
- Find your cloud infrastructure
Gain Continuous Visibility
For continuous cloud access audit and compliance reports
- See which apps are being used
- See which resources are being used
- See what data is being accessed
- See active identities and permissions
Uncover Vulnerabilities from Exploitable Access
For access posture management and continuous access governance
- What application risks exist?
- What data risks exist?
- Who are risky access identities?
- What are risky roles?
Prioritize and Remediate
To act quickly on what matters to your business and enrich your governance
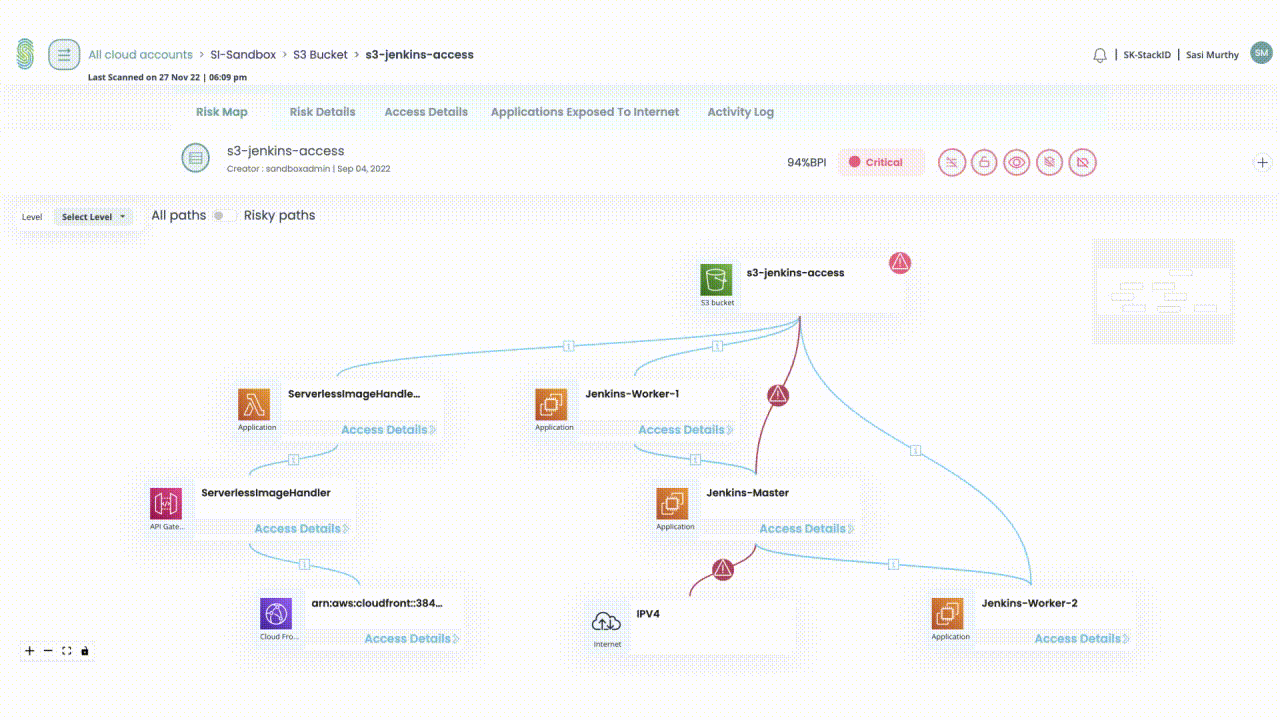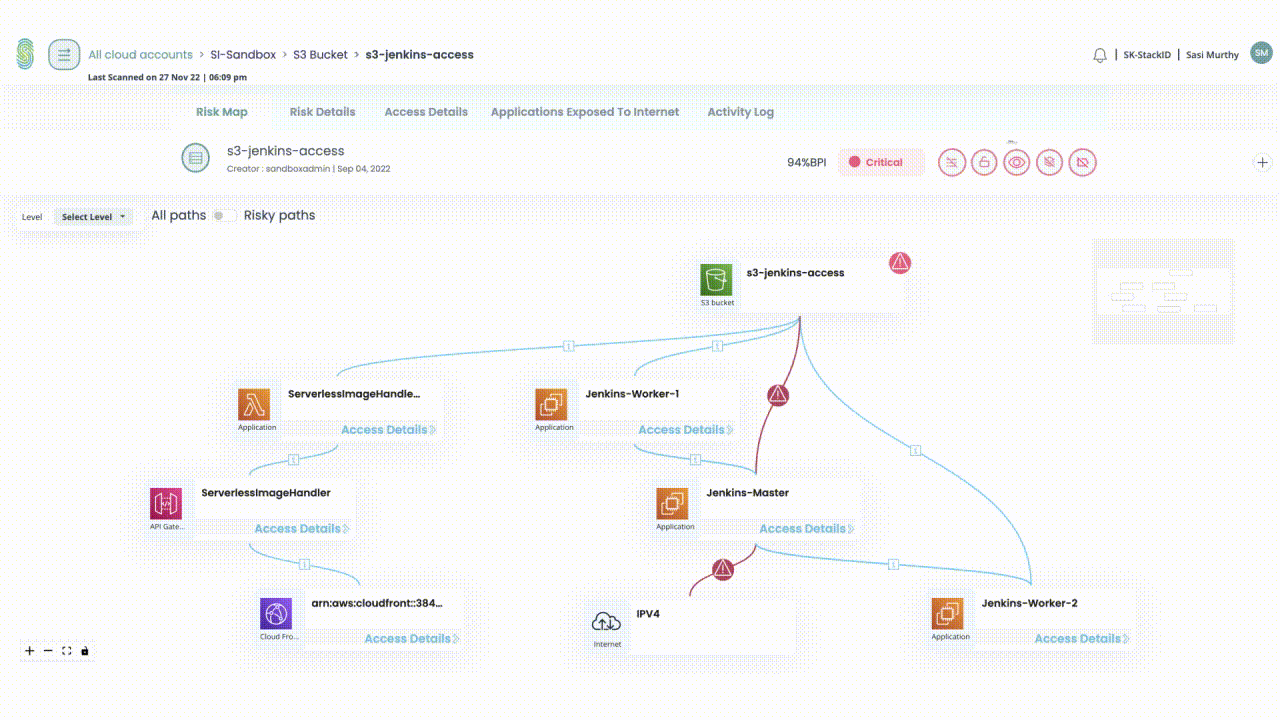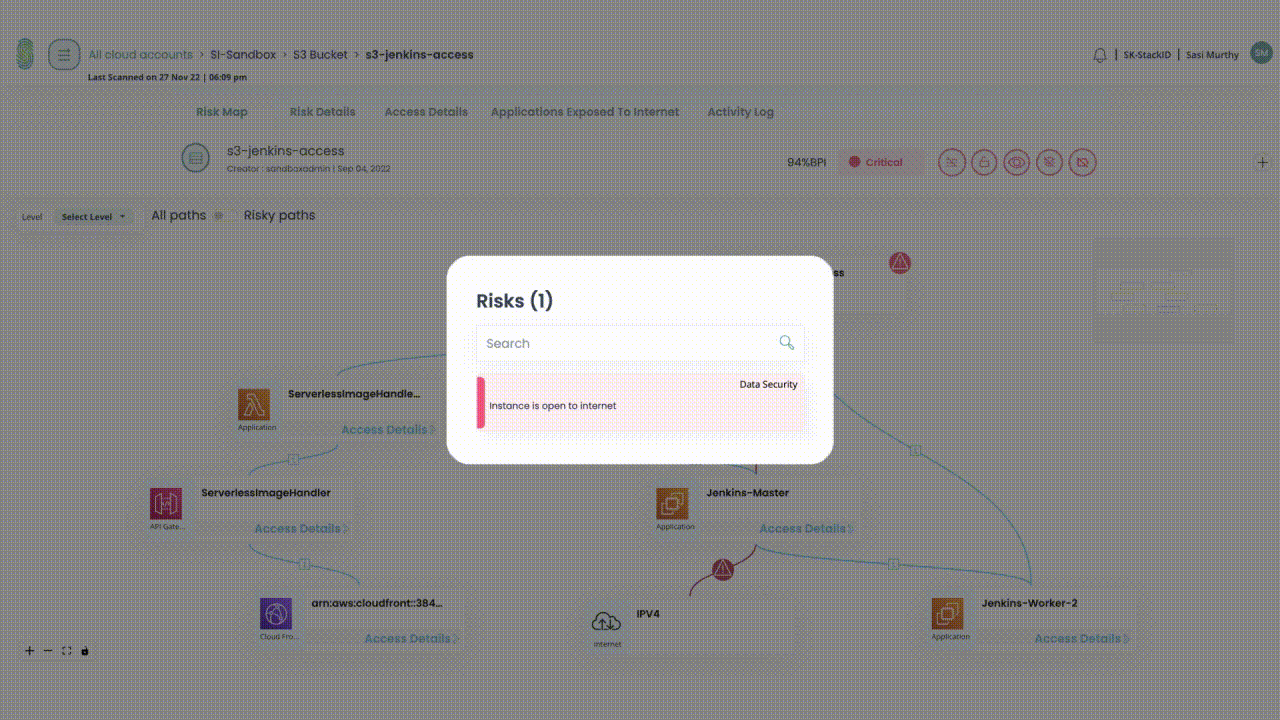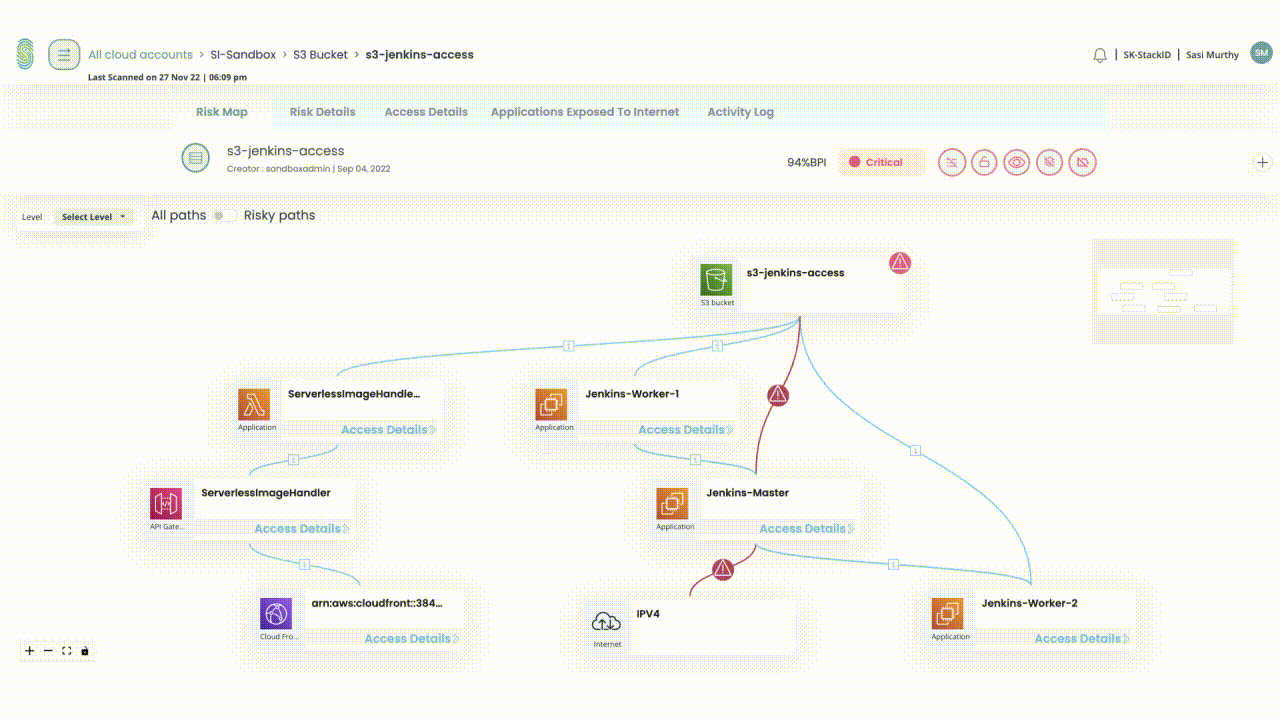
- Identify the most exploitable access paths
- Which exposed EC2 instances are at the highest risk?
Due to:- Pathways to sensitive data
- Frequency of access
- External exposure
- Over-provisioned access
- Action risky access and permissions quickly