Blogs
Four transformational approaches to improve the efficacy and efficiency of User Access Reviews - a foundational ...

Earlier this month, Ken Foster, VP of IT Governance, Risk and Compliance - FLEETCOR and Al Ghous, former CISO ...
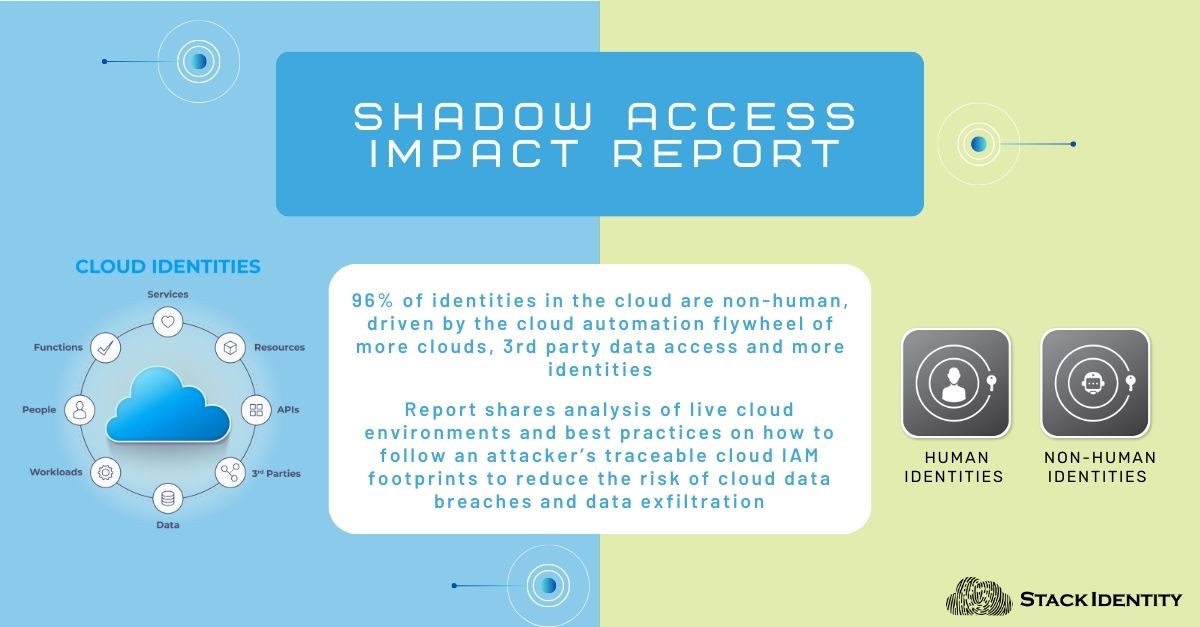
Summary: This Stack Identity Shadow Access Report outlines the risks created by thousands of dynamically changing ...

We understand the importance of security and wanted to start with SOC-2 compliance to implement basic security for our environment.
Stack Identity has achieved Validated Partner status and passed the AWS Foundational Technical Review for its ...

By Venkat Raghavan and Dr.Prakash Shetty
This report is an analysis of IAM activities undertaken by the ...

By Stuart Horne Security teams complain that they are overwhelmed with existing cyber security initiatives when it ...

Digital supply chains and data power our digital economy. Conceptually similar to physical supply chains, digital ...

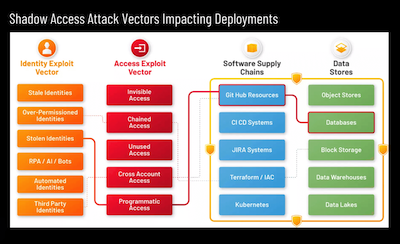
By Venkat Raghavan, Founder & CEO, Stack Identity Shadow Access is unmonitored, unauthorized, invisible, ...
By Rupa Parameswaran The cloud software development ecosystem operates in a complex and dynamic environment where ...
Kicking off 2023 for Stack Identity, our founder and CEO Venkat Raghavan was a guest speaker at the Bay Area OWASP ...
By Venkat Raghavan
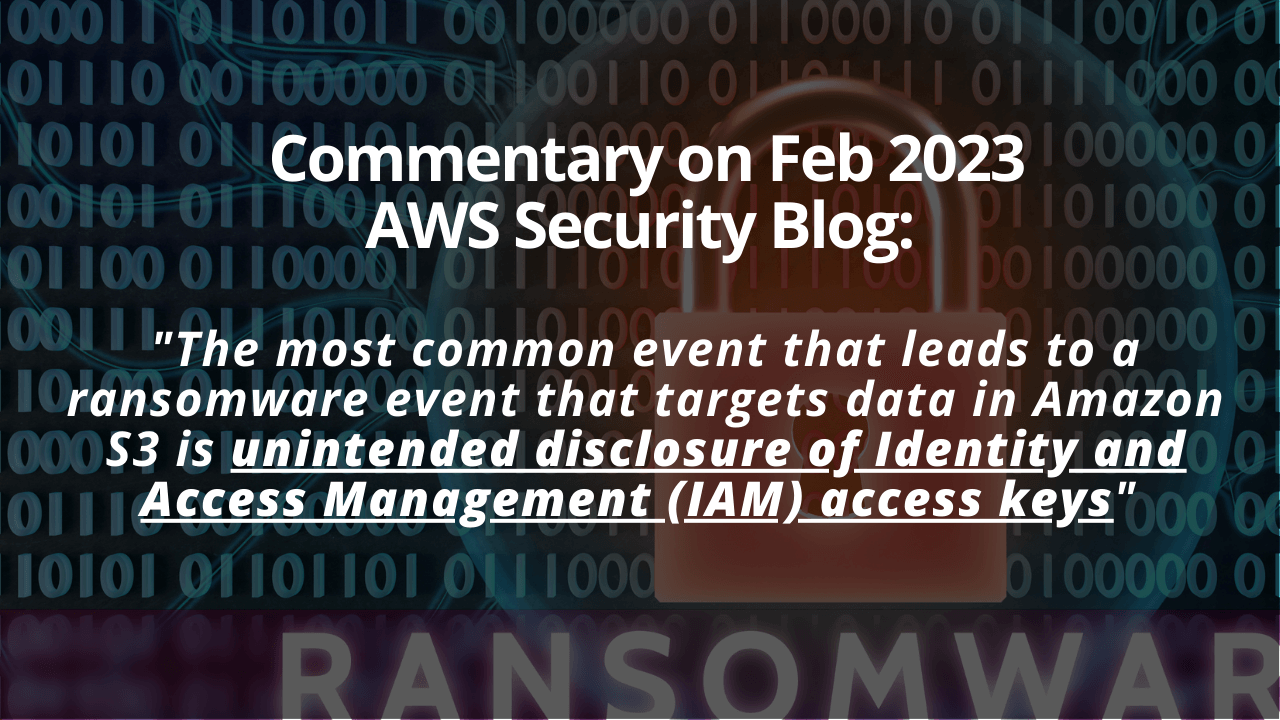
Over the weekend I read a very interesting and informative blog from AWS “The anatomy of ...
