Shadow Access Ebook
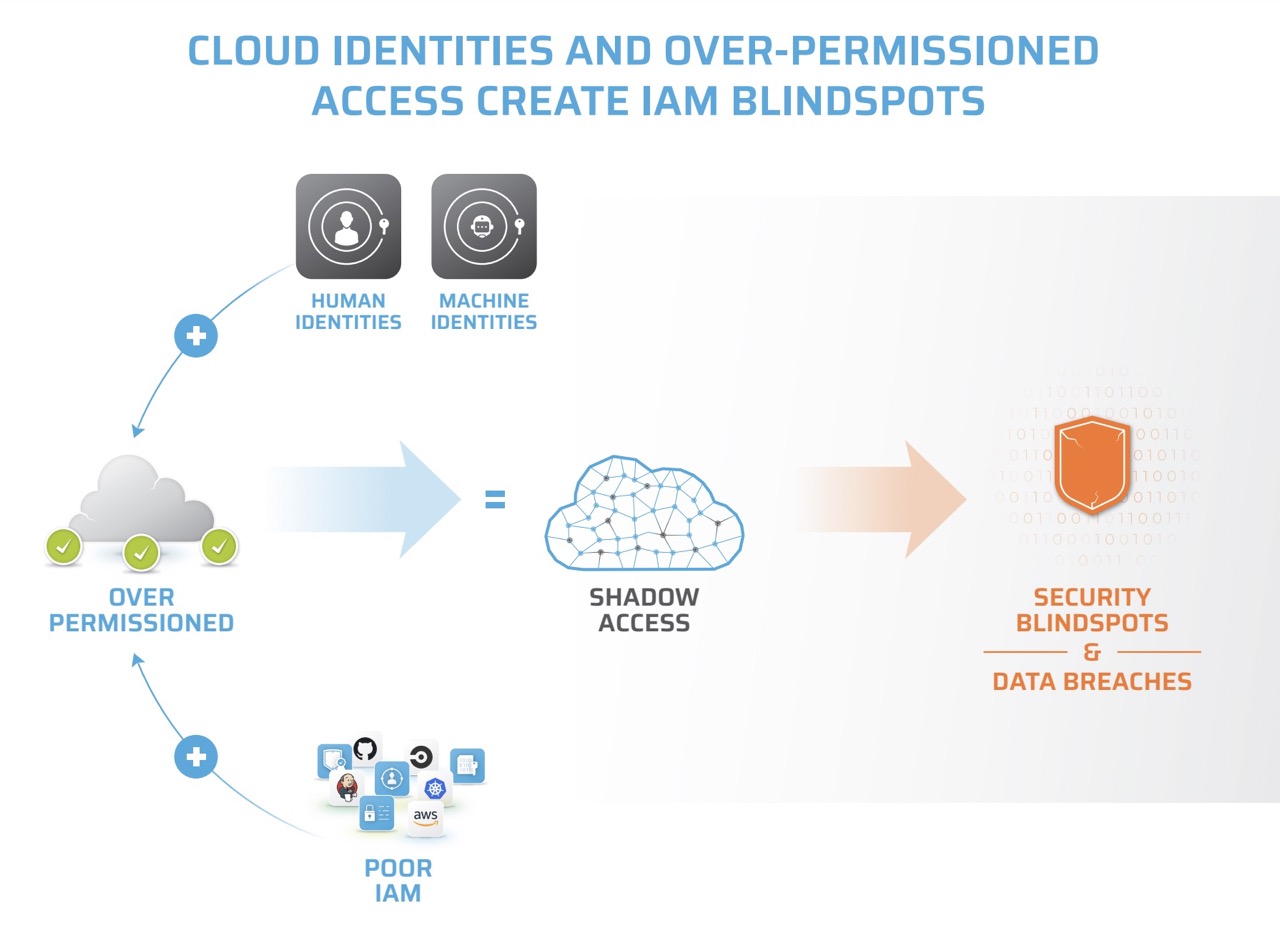
80% of cloud breaches are attributed to IAM blindspots that attackers exploit. These breaches are entirely preventable by fixing Shadow Access. Governance, security operations, and data owners are all impacted by Shadow Access risks.
In this ebook, learn:
- What is Shadow Access and what causes it?
- How do attackers leverage cloud identities, access permissions, and entitlements?
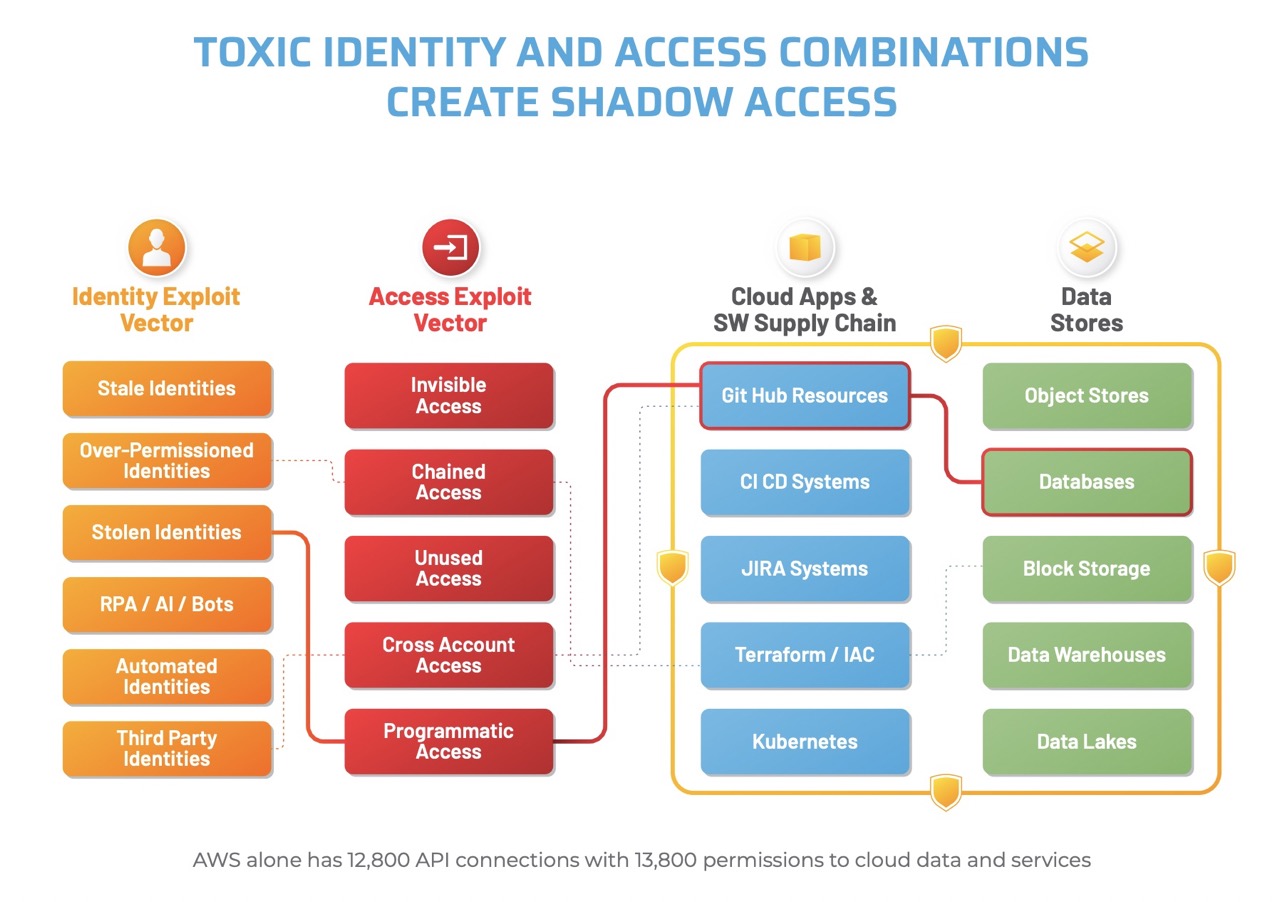
- What are the 10 types of Shadow Access?
- How to address cloud IAM problems?
- How does Shadow Access impact DevOps, SecOps, and data owners?
After reading this ebook, you will understand the best practices that allow you to proactively deal with Shadow Access, help remove long-standing privileges and provide solutions to prevent exploitable access.