Data Attack Map
A dynamically updated map of cloud data security risks to enable active and timely remediation
Stack Identity comprehensively detects cloud data security risks across identity, access and applications. This integrated view of risks across traditionally siloed data security vectors creates a meaningful and accurate view of your risk posture, and enables comparison and prioritization of different data breach pathways.
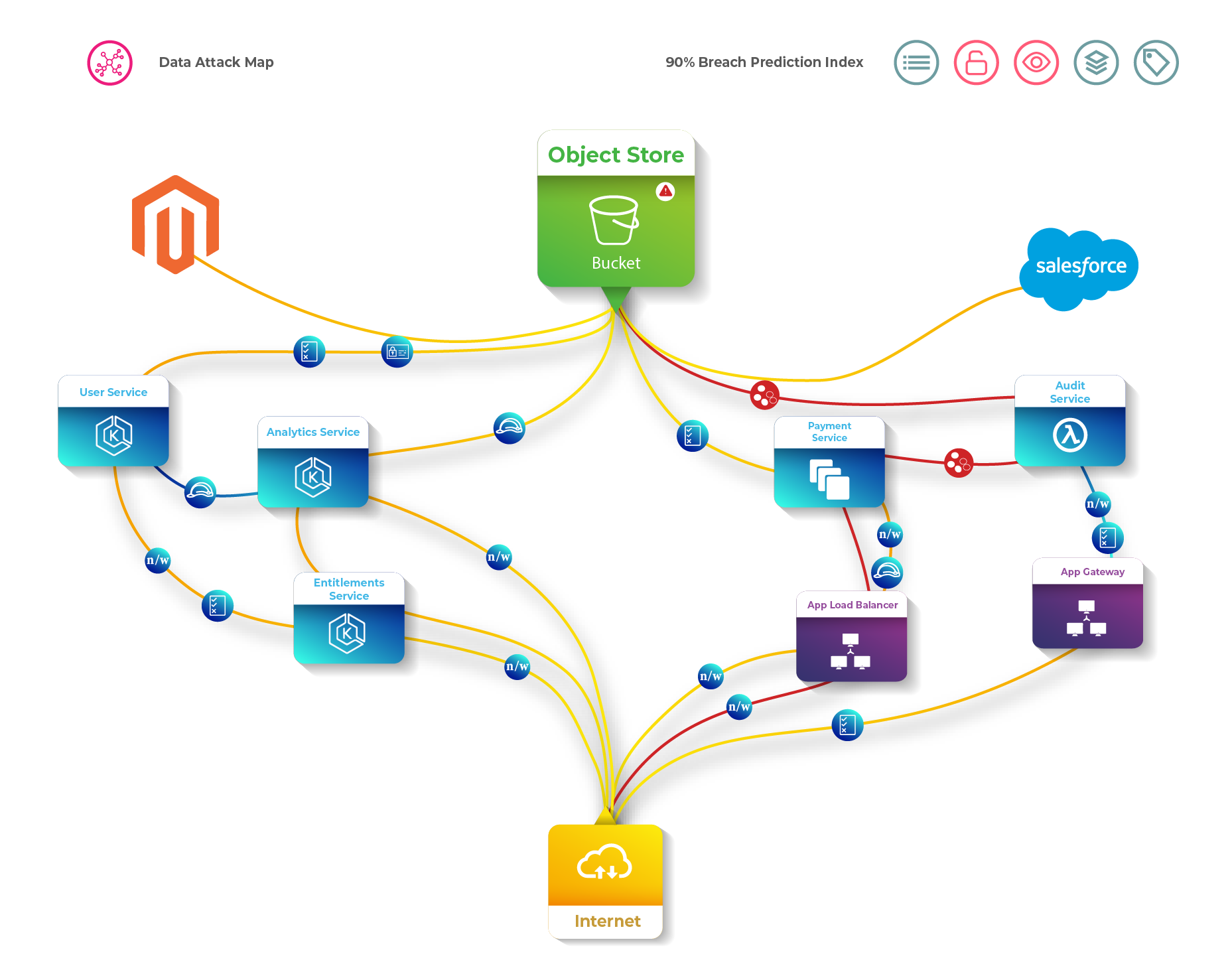
The live data attack map dynamically displays a color-coded and prioritized view of breach pathways. The breach prediction index is determined by different vulnerabilities such as over-privileged access, invisible access to cloud, excessive and unused access. This enables constrained security teams to focus on the highest risk vectors that need to be prioritized for timely remediation.
Cloud security teams can also integrate the prioritized vulnerabilities and automatically configure notifications and workflows in order to actively remediate against dynamically changing cloud data security risks.
How it works
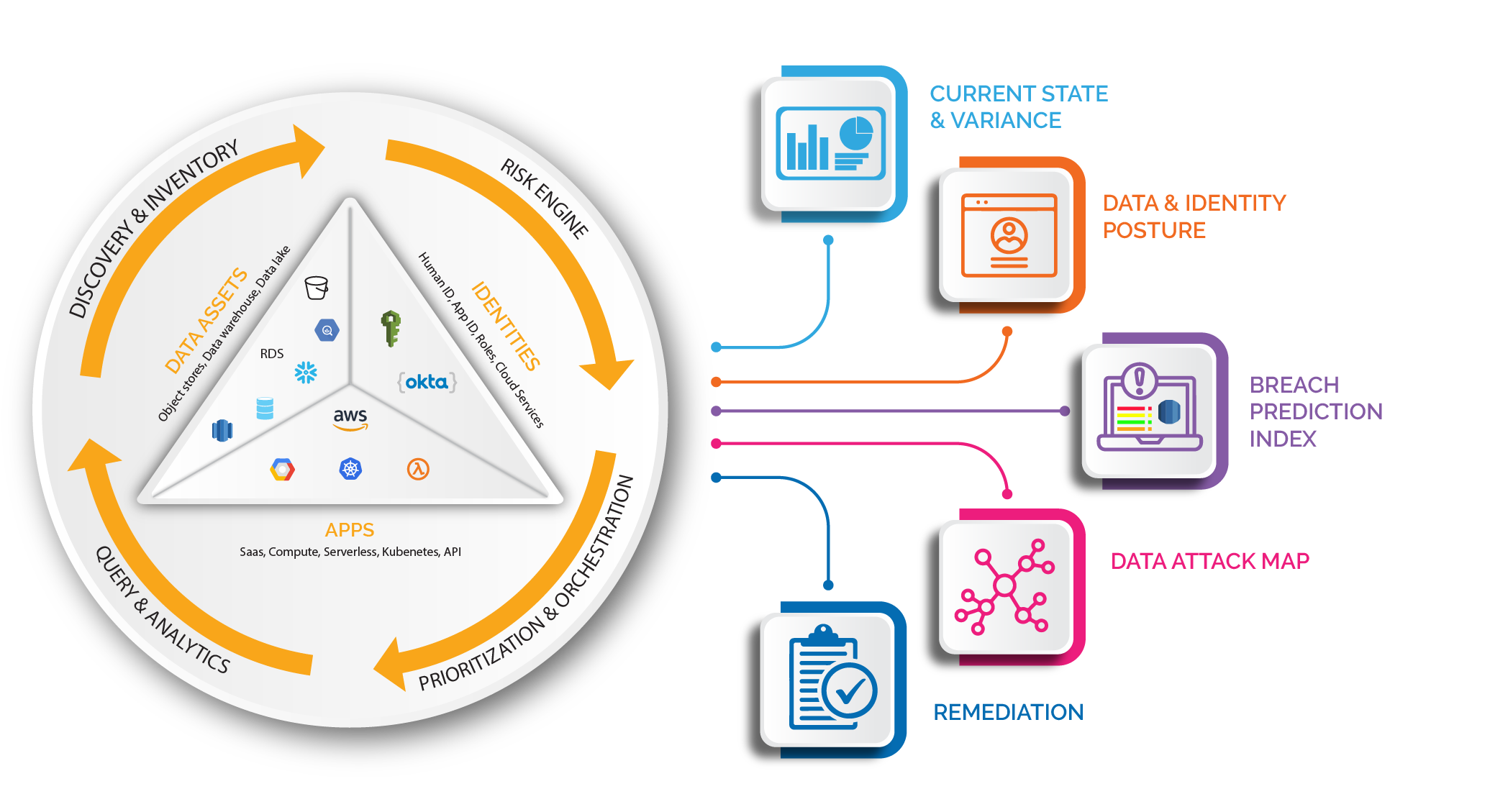
Stack Identity continuously monitors vulnerable cloud data stores revealing unmonitored, ungoverned and unsafe access that impacts your audit, security and compliance exposures.
Stack Identity continuously tracks IAM vulnerabilities in cloud native environments. This enables Cloud and SecOps teams to identify all vulnerable pathways by which data can be exfiltrated, track external data sharing, and reveal unauthorized access. Our platform provides guided automation for remediation and a preventive “shift left” approach.
To create a live data attack map Stack Identity performs the following functions:
- Discovery & Inventory: Dynamically discovers all cloud data stores and automatically maps identity, access and application connections
- Risk Engine: Multi-dimensional risk engine continuously tracks IAM vulnerabilities revealing constantly changing patterns of cloud data vulnerabilities
- Risk Prioritization and Orchestration: Delivers a risk-driven prioritized view of vulnerabilities based on exposure and exploitability with the ability to orchestrate recommendation actions and remediations via notification workflows
- Query and Analytics: Ground truth operational data to understand the “why” of IAM and data vulnerabilities
Stack Identity readily assesses your cloud data and identity risks, enabling cloud security teams to specifically pinpoint and actively remediate dynamic cloud security risks.
Current Data Security Status
Assess Data Identity Posture
Breach Prediction Index
Live Data Attack Map

