The explosion of identities, permissions, and credentials is sweet music for attackers and adversaries. They don’t need to hack into systems, they can simply log in with legitimate access. We have seen this singular pattern from the massive Capital One data breach in 2019 to the latest Microsoft data breach on January 12th, 2024. This is also substantiated by the 2023 Verizon data breach investigations report (DBIR) which revealed that 80% of cyber-attacks leverage identity and access-based techniques. Identity is now the biggest attack vector.
Let’s assume an enterprise with 10,000 employees. On average, each employee has four login accounts, five devices, and three locations from which they access enterprise data. That’s 600,000 legitimate pathways enterprises have to continuously monitor for identity risks daily across their twenty-plus disparate identity and access systems. Add to it the access, APIs, service accounts, and your contractors’ needs. Identity is the biggest attack vector. The rise of digital identities and shadow access is driven by a new era of applications powered by Data, AI, and Automation. Gartner states that all cloud infrastructure and resources are “Super Identities.” In 2023, 75% of failures were a result of inadequate management of identities, access, and privileges, up from 50% in 2020.
This underscores the critical importance of effectively managing identities, permissions, and credentials to mitigate security risks in today’s digital landscape. The speed and scale at which identities operate today, cannot be managed by manual efforts or quarterly access reviews. Neither can you expect your SOC analysts to collect all logs to proactively stop breaches; at most, they can help you in the forensic analysis of your breach. You need an automation tool as a copilot to help you address these issues proactively.
Here’s how organizations can address the challenges posed by the explosion of identities and the increasing sophistication of cyber threats:
-
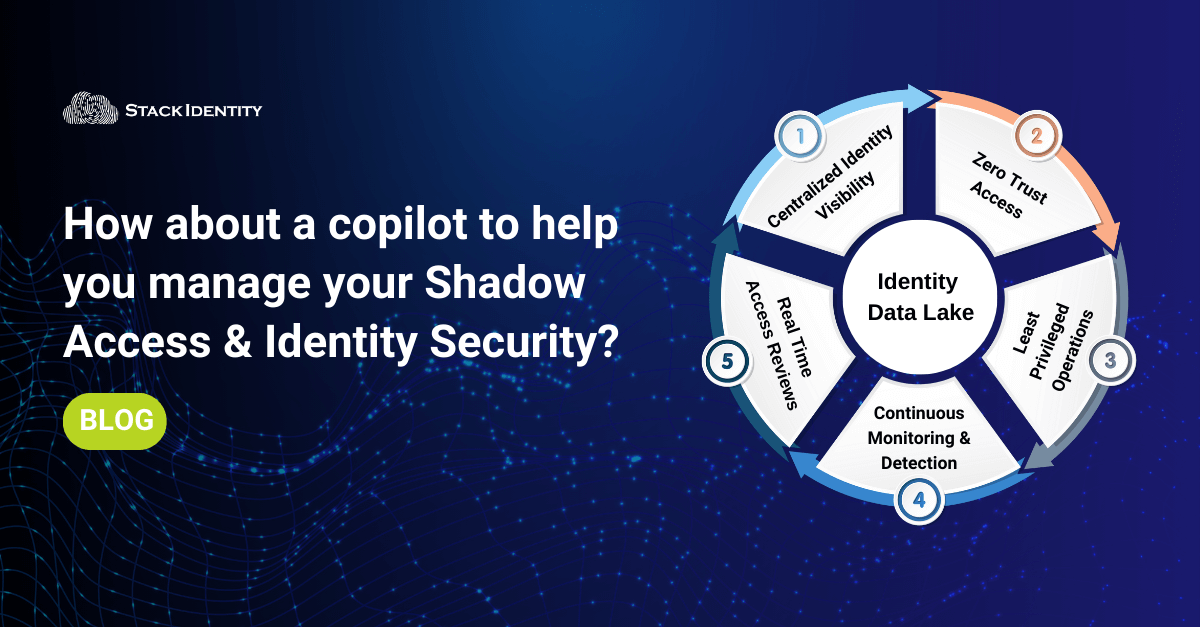
Centralize Identity Visibility:
Shadow Access is the biggest challenge security teams face today. To address this issue Implement a centralized identity Visibility solution to identify all user identities, access rights, and authentication mechanisms centrally across your employees, contractors, application APIs, service accounts, Local identities (not covered by IDPs) machine identities, etc. This enables better control and visibility over all access across the organization. Your foundation will have blind spots unless you have complete visibility into every identity in your environment.
-
Zero Trust Access:
Embrace the Zero Trust Access model, which assumes that no user or device should be trusted by default, regardless of whether they are inside or outside the corporate network. Emphasize continuous verification and strict access controls based on identity, device health, and contextual factors. Rectify things on an immediate basis to avoid future risks.
-
Least Privileged Operations:
Apply the principle of least privilege to limit user access to only the resources and data necessary to perform their job functions. Review and update access permissions based on changes in roles or responsibilities and rightsize the permissions based on actual usage.
-
Continuous Monitoring and Detection:
Detect anomalous behavior, unauthorized access attempts, and suspicious activities across the enterprise’s digital ecosystem. Implement real-time alerts and response mechanisms to mitigate threats promptly.
-
Real-Time & Dynamic Access Reviews:
Perform real-time audits and assessments, to identify vulnerabilities, misconfigurations, and weaknesses in the organization’s identity and access management infrastructure. Use the findings to remediate issues and improve overall security posture.
You may have implemented multiple tools over time but they still require manual effort and throw thousands of alerts that can never be fixed. Imagine all these done automatically using Stack Identity Copilot to reduce 90% of your manual efforts and proactively help you fix the challenges.
By adopting a holistic approach to identity and access management, organizations can better protect themselves against the evolving threat landscape and minimize the risk of data breaches and security incidents.
