
This rise of cloud-native applications gave way to a plethora of cyber security solutions, some extended from the traditional on-prem world and some – born-new to serve the age of the cloud. To educate the industry at large, analysts have created more and more categories and classified these solutions into various trendsetting segments such as Cloud Monitoring, Cloud Security Posture Management (CSPM), Cloud Workload Protection (CWPP), Cloud-Native Application Protection Platform (CNAPP), SaaS security, Data Security, Data Monitoring, Cloud Infrastructure Entitlement Management (CIEM) and many more. Yet these categories do not cover the problem of governance in the cloud.
So, what is the problem you ask?
Half a decade ago, in the times of older (on-prem) technology, an identity (human, application or a machine account) creation and access provisioning was a Governance before Operations procedure. Identity and Access requests went through a defined process for approvals. There was a methodical change management process for access that provided visibility into identity risk. Every identity and almost all access was visible through the governance lens. Any outlier identity or access had to go through an exception process with sign-offs for accountability. The operational environment was controlled because organizations had excellent ground truth of who had access and how it was issued, and how often it was used. May not be 100% accurate, but there is governance nonetheless!
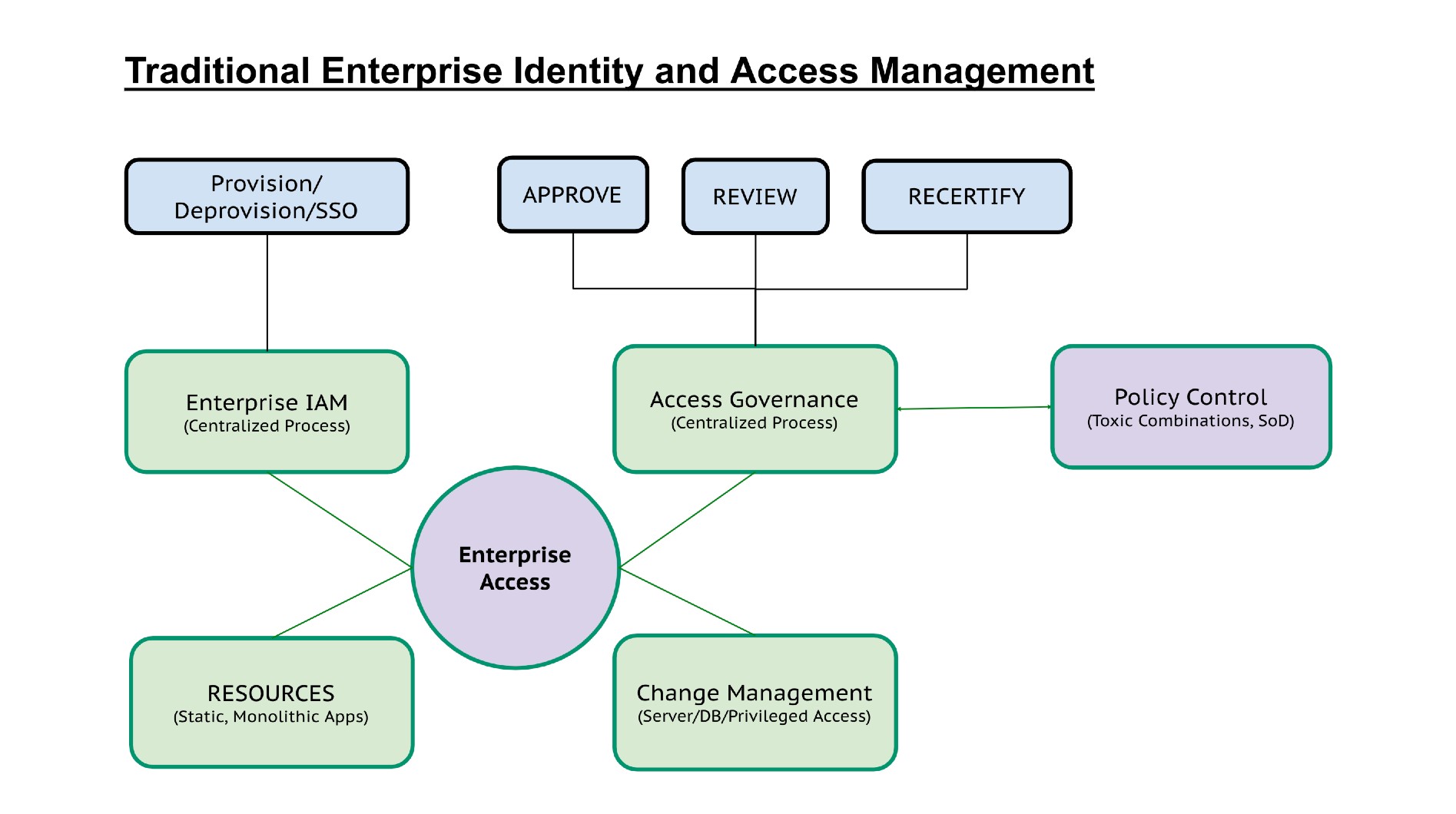
Now ask yourself a question – how many access-related misconfiguration breaches have you heard of prior to cloud technology? Very few, the reason being that on-prem access to sensitive and confidential data is well-governed through a controlled process.
Are we suggesting that we should go back to the Stone Age?
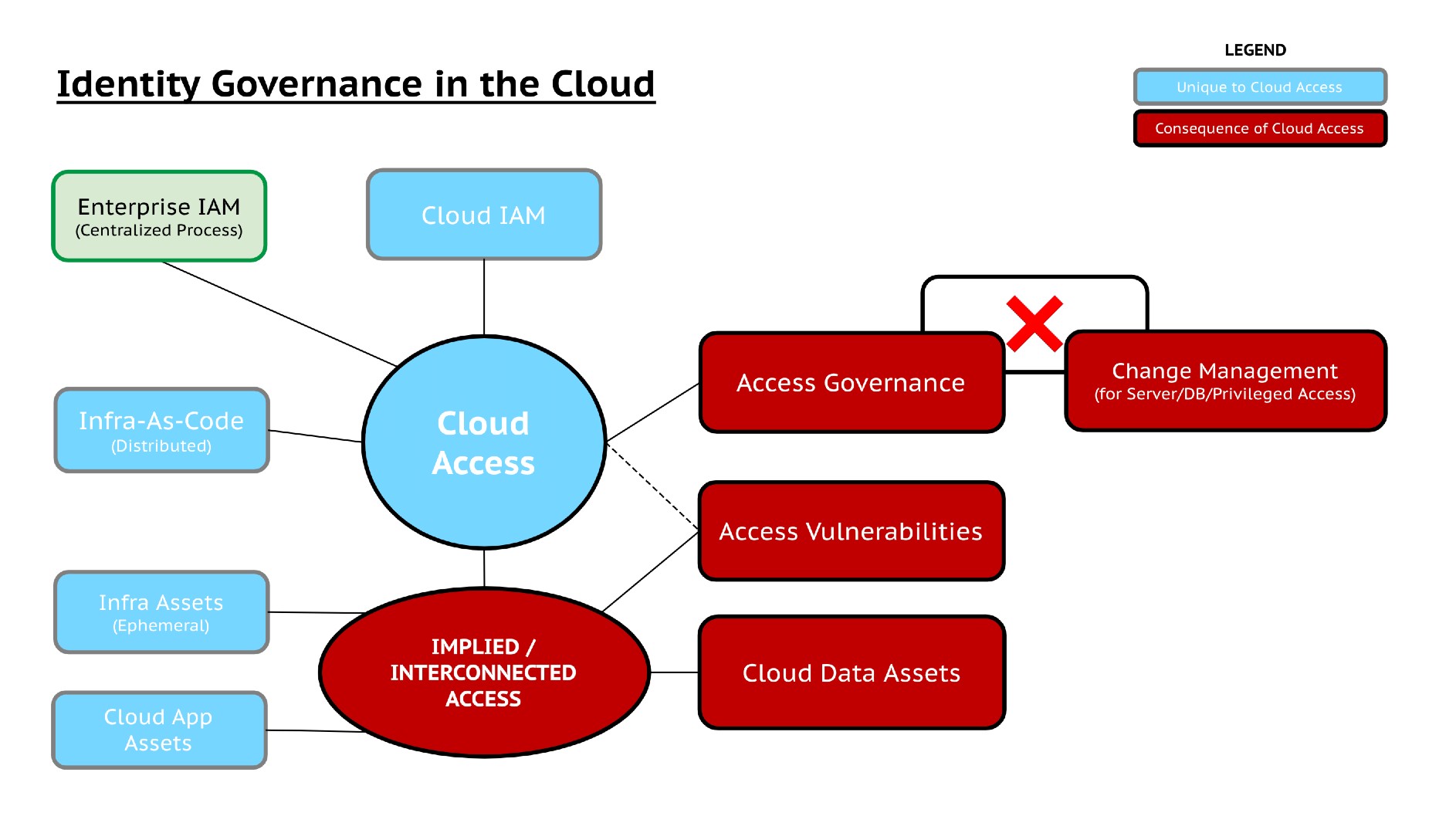
Absolutely not, your users of click-of-a-button IAC tech will not let you go back to the past even if you wanted to. All we are saying is that the rise of cloud applications brought an earth-quake-level procedural shift to how applications are developed, how policies are enforced, and how infrastructure is managed. This massive shift occurred very quickly and overlooked the foundational security control of “Identity Governance”. The FOMO mindset that was created in many organizations forced them to adopt cloud strategies (let us call them victims of the cloud quake) – and adapt to “insert your favorite acronym” cloud-native, COTS solutions. These solutions mostly focused on cloud configuration postures (CSPM) & ease of infrastructure management (IAC), but never took into consideration how the fundamental governance process is translated to the cloud. The result is that a Governance-First model is now lost and rapid cloud adoption has created an Operations-First model.
So, what is the path to enlightenment?
Continuous Governance is the way forward. There has always been an inherent conflict between users’ needs and security requirements, and now the cloud enables a wide range of options with greater ease of use that puts robust security into a more precarious situation. Historically, a fair compromise of this battle was Security Governance & Control Operations where the pace of access and governance was primarily controlled by procedures. With the cloud, the excessive demand for access and lack of governance coupled with the lack of visibility into identity and data risks creates a void that can only be filled through continuous governance.
The notion is not to reject CSPM, SSPM, CWPP and other security tools. They are necessary to have general visibility and purpose-driven operations. However, these solutions are largely focused on infrastructure and configuration and do not provide visibility of risk to the most important asset, the data, and the governance of identities that can access these data assets.
Let the pace of application development, and access provisioning continue the way it is, but it is necessary to evolve and build an element of continuous governance into the process. My recommendation for this paradigm of continuous governance is one that is strongly grounded in detection and response engineering focused primarily on identities and their access to data by:
- Continuous monitoring of who HAS & who IS accessing your data assets
- Detection of attack paths to critical resources & remediation
- Quantifiable risk scoring of data assets and identities
- Prioritizing remediations based on the risk of exposure and exfiltration of data
- Measuring the maturity of policy enforcement & violations
As the demand for access to resources and data in the cloud grows, identity governance must evolve away from a discrete process of governance before operations to a process of continuous governance. Visibility of cloud data access risks focused on data and identities is the path forward to security and governance in a cloud-native environment.
