Introduction to the Shadow Access Report
Zettabytes of data pouring into the cloud has led to a proliferation of data stores containing sensitive information. As more cloud applications and services are created to leverage this data, more identities are generated, causing in turn more access to data. AWS alone has thousands of connection methods that can use thousands of permissions, creating millions of access combinations.
Stack Identity has published the industry’s first report on Shadow Access and its impact on cloud security, governance, and operations. The research uncovers some key insights:
- Human identities are no longer the primary identities in cloud environments, and machine identities have dramatically overtaken human identities by a ratio of 20:1.
- The mathematics of millions of access combinations and how identity and access exploit vectors create risky pathways traversing cloud apps and the software supply chain exposing sensitive data in cloud data stores, databases, and data lakes.
- The 10 different types of Shadow Access that give attackers the ability to infiltrate cloud environments and exfiltrate sensitive data.
- Findings of Shadow Access risks in live customer environments and how these weaponized pathways exploited cloud environments, created cloud security risks and impacted business efficiency.
- Best practices and recommendations on how to improve cloud security risk posture and regain control of IAM in the cloud.
Why Shadow Access is Pernicious in Cloud Environments
To the average company utilizing cloud services, what worked before, especially in on-premise environments does not work in cloud environments. With the rush to migrate to the cloud and utilize more cloud services, access has been pulled along to keep pace, leaving governance of identities and access controls left behind.
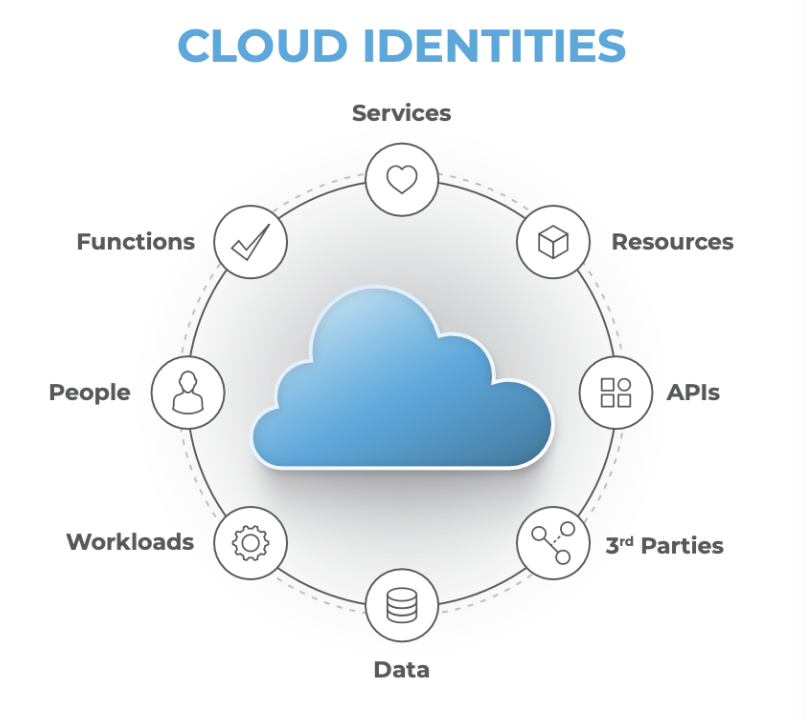
This is due to the sheer volume of identities that exist in the cloud; in the past, in on-prem environments, identities were primarily tied to the number of human identities. In the cloud, identities are automatically created for multiple purposes: for API access, 3rd party access, data access and data sharing, along with the creation and management of workloads, services, and resources. The rate of change for identities and access permissions in the cloud creates a complexity of access control that completely causes existing security, compliance and governance processes to be upended.
Shadow Access in Live Cloud Environments Creating Data Breach Risks
Stack Identity uncovered multiple instances of Shadow Access in live cloud environments, by proactively analyzing identity and access data collected from across multiple cloud data, identity, and data resources.
| Cloud Breach | Invisible access by an attacker due to the fact that the AWS policy console does not show effective permissions or inherited permissions to an identity or resource. |
|---|---|
| Cloud Breach | A compromised resource-based policy created a back door for an attacker to access the cloud environment. |
| Cloud Breach | A server-less (Lambda) function was replaced with malicious code that added an IAM user for an attacker’s access from outside. |
| Cloud Data Exfiltration | Abused IAM permissions attached to an application instance or application running on a compute instance in the cloud was used to exfiltrate sensitive data. |
| Cloud Breach, Malware Hosting | Programmatic access to an external vendor was compromised that caused S3 to be used for crypto mining and malware hosting. |
To learn more about the impact of Shadow Access download the report here
To assess the impact of Shadow Access in your cloud environment, register to download your assessment tool here: www.stackidentity.com/Shadow-Access-Risk-Assessment.
