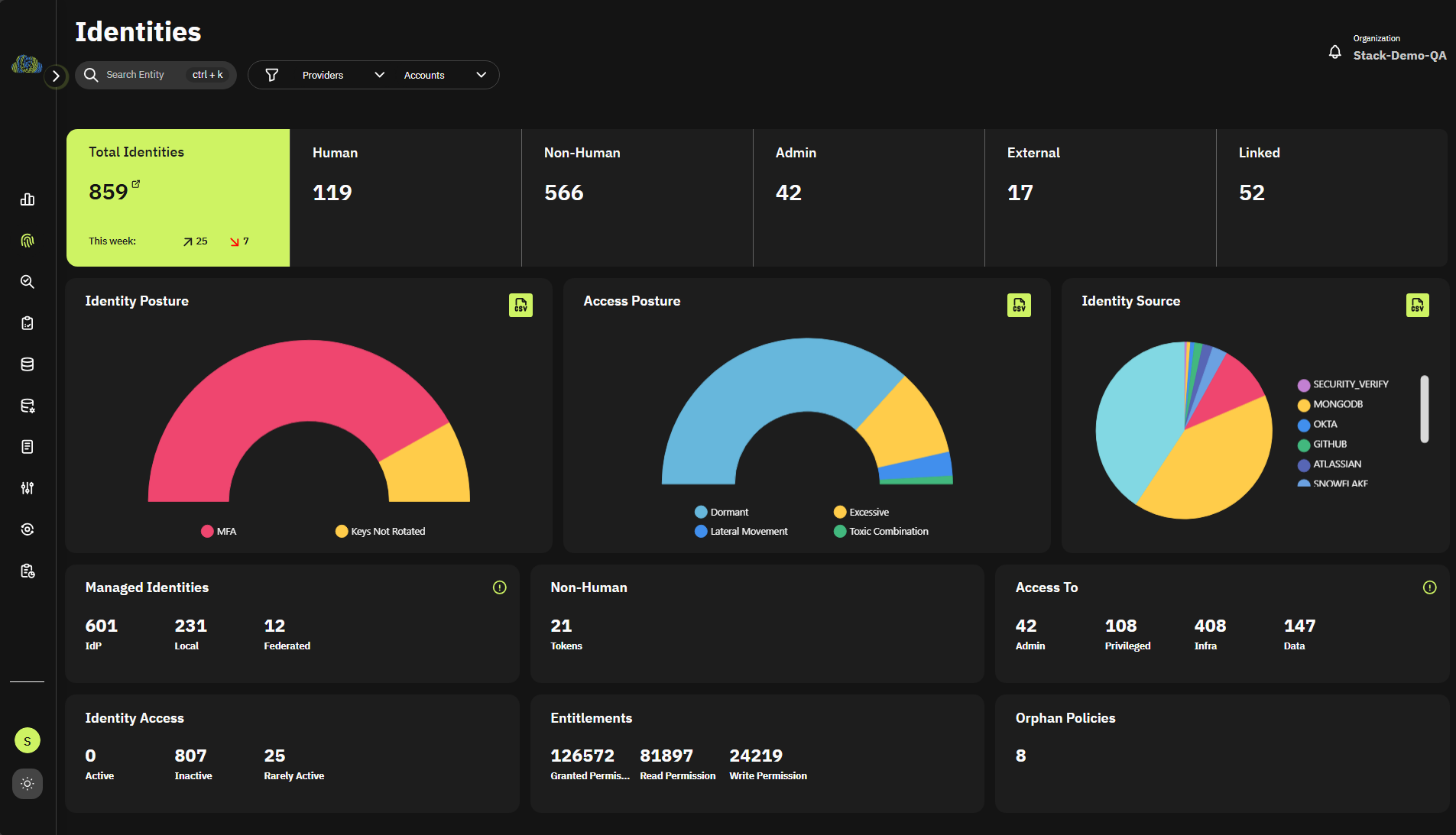
How Stack Identity can help:
- Build an active inventory of the non-human identity population across your IDP, Cloud environments workload & databases
- Visualize via access graph NHI access pathways and access to critical resources
- Analyze NHI exposures:
- Key rotation gaps
- Orphaned credentials
- Delegated Access
- Take action:
- Clean up unused, dormant, and risky creds
- Convert static secrets (credentials) to Just in Time credentials
- Right size over privileged credentials
- Generate audit reports for DevOps and identity teams
Benefits:
- Eliminate Key rotation
- Reduce attack surface
- Get ahead of security incidents
- Automate compliance reporting
