- Daily report of prioritized Shadow Access risks in your environment
- Automated analysis of identity security risks with contextual evidence
- Eliminate the need to stitch together piecemeal, manual tools
- Supports secure environments, No external credentials required
What is SARA?
The Stack Identity Shadow Access Risk Assessment (SARA) eliminates the need for piecemeal, manual tools and processes and enables you to proactively detect identity security risks in your cloud environment and easily answer:
- What new cloud operations risks have occurred in the last 24 hrs?
- Any permission changes or privileged access operations?
- Where and why are IAM policy violations happening?
- Has there been risky access to production systems?
- What new identity security risks have occurred?
How does SARA work?
The Shadow Access Risk Assessment (SARA) utilizes Stack Identity’s patent-pending, proprietary product algorithms to comprehensively assess and analyze different cloud events and identify new Shadow Access risks. It is a stand-alone, lightweight version of the Stack Identity enterprise platform designed to only run in your cloud environment.
How do I get a SARA in my cloud environment?
- Register here
- We send you the SARA reporting tool
- You install the SARA reporting tool in your cloud account
- You configure account and email settings for SARA
- Daily Shadow Access Risk reports are sent to your inbox

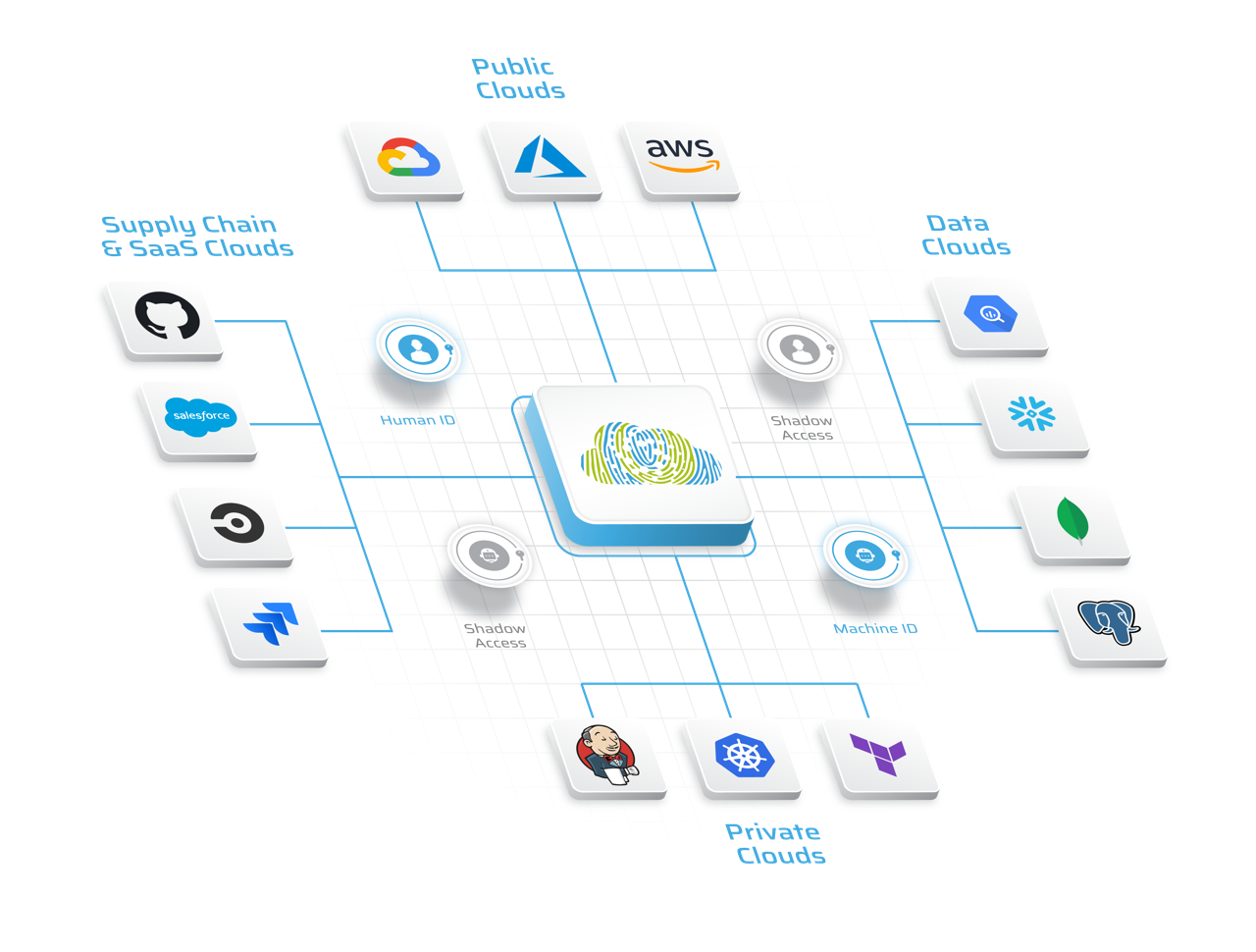
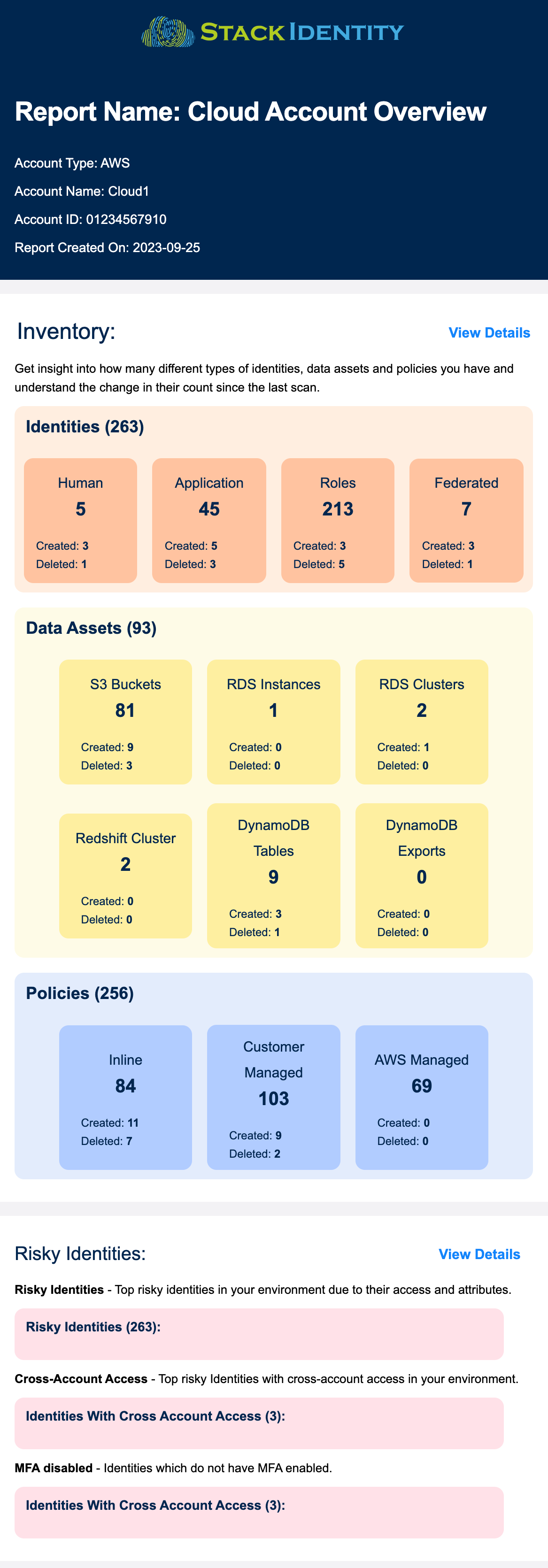
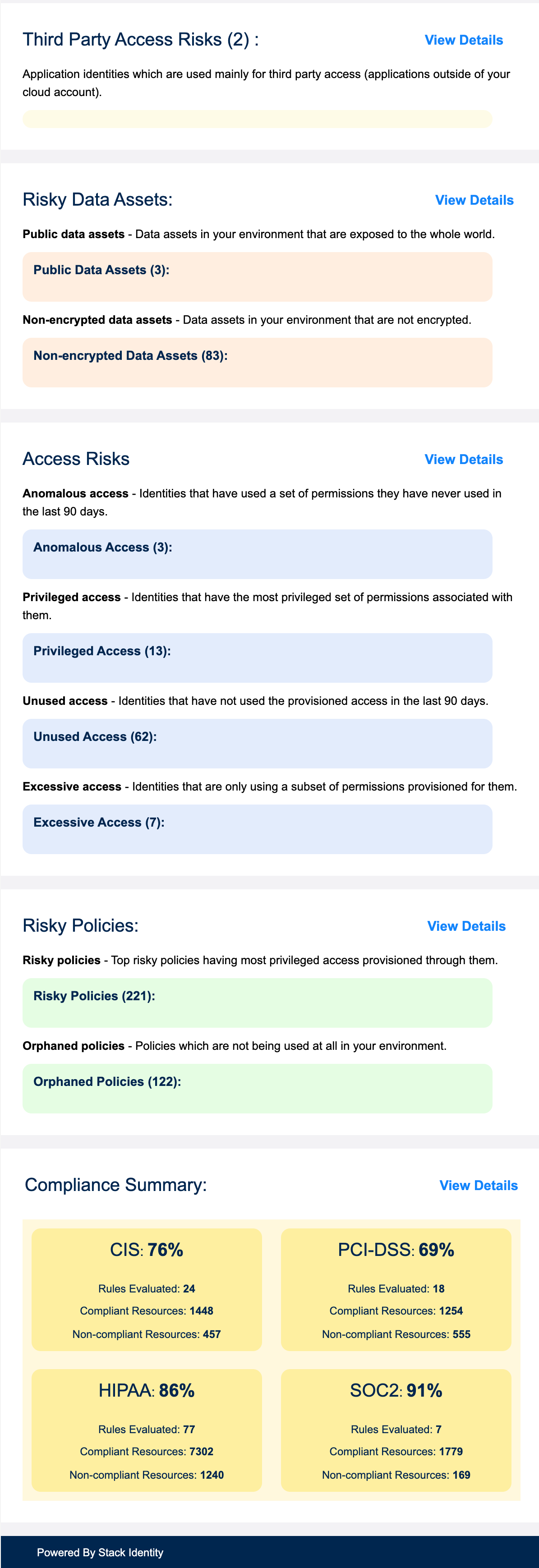
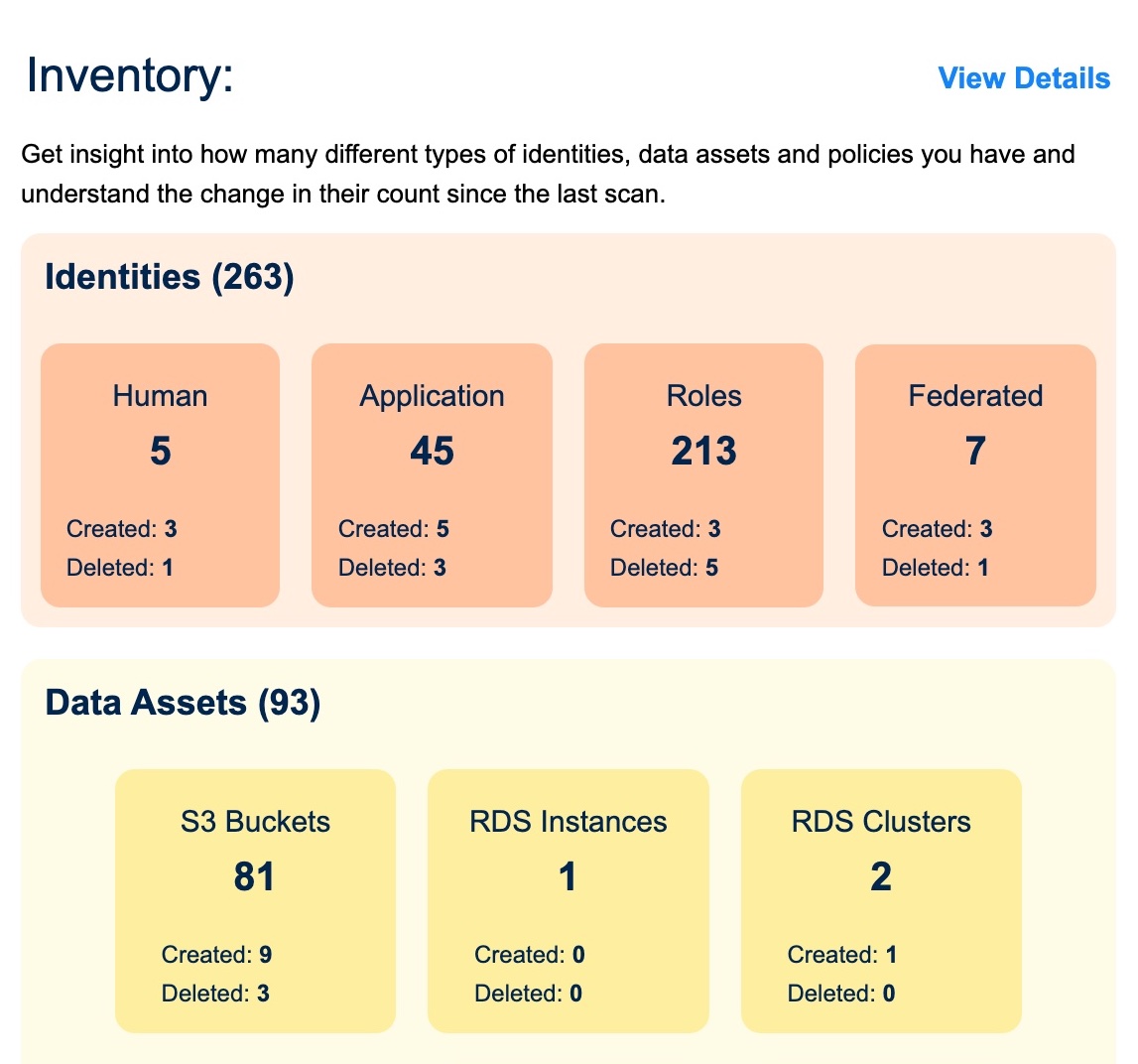
You will receive a daily report of Shadow Access Risks with insights about your environment, for example:
- The number of identities, data assets and policies you have
- Top risky identities due to their access and entitlements
- Application identities being used for third-party access
- Data assets that are exposed to external networks
- Cloud identities that have not been used in the last 90 days
- Daily compliance scorecard for CIS, PCI-DSS, SOC2 and HIPAA
Report Samples