Unified Platform
Powered by the industry’s first Identity Security Data Lake which consolidates, correlates and contextualizes identity, access risks and vulnerabilities across cloud and data estates.
Open API platform
Data enrichment and analytics that enables you to detect, remediate and govern what matters most to your business.
Automated detections
Identifies toxic combinations, chained access, lateral movement, drift detection, overprivileged, unauthorized shadow access and shadow identities and policy violations.
Extensible platform
Integrates into your multi-cloud environment, IDP systems, ticketing systems, SecOps, IAM and GRC processes.
Our platform is built upon an IAM Data Lake to answer the most pressing security questions in your multi cloud environments
with speed and simplicity.
How it works
Stack Identity has developed an AI-powered identity security platform to combat identity attacks. Our patent-pending innovation would have prevented the UNC 5537 threat campaign. The platform builds an AI-powered data trail to uncover exposed data assets vulnerable to identity attacks, misconfigurations, and least privilege exposures.
Stack Identity’s platform integrates ITDR, ISPM, CIEM and SaaS entitlements, continuously monitoring data risks and vulnerabilities from compromised identities, credentials, and unauthorized privileges.
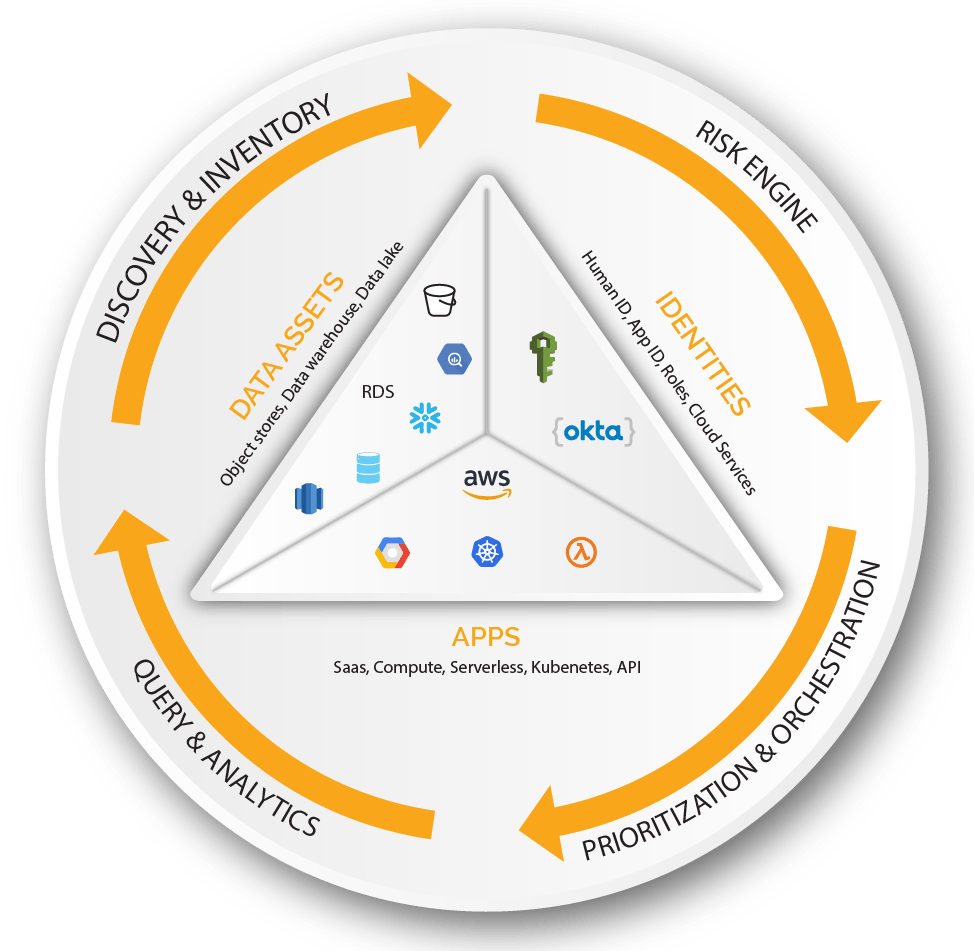
- Discovery & Inventory: Dynamically discovers all cloud data stores and automatically maps identity, access and application connections
- Risk Engine: Multi-dimensional risk engine continuously tracks IAM vulnerabilities revealing constantly changing patterns of cloud data vulnerabilities
- Risk Prioritization and Orchestration: Delivers a risk-driven prioritized view of vulnerabilities based on exposure and exploitability with the ability to orchestrate recommendation actions and remediations via notification workflows
- Query and Analytics: Ground truth operational data to understand the “why” of IAM and data vulnerabilities
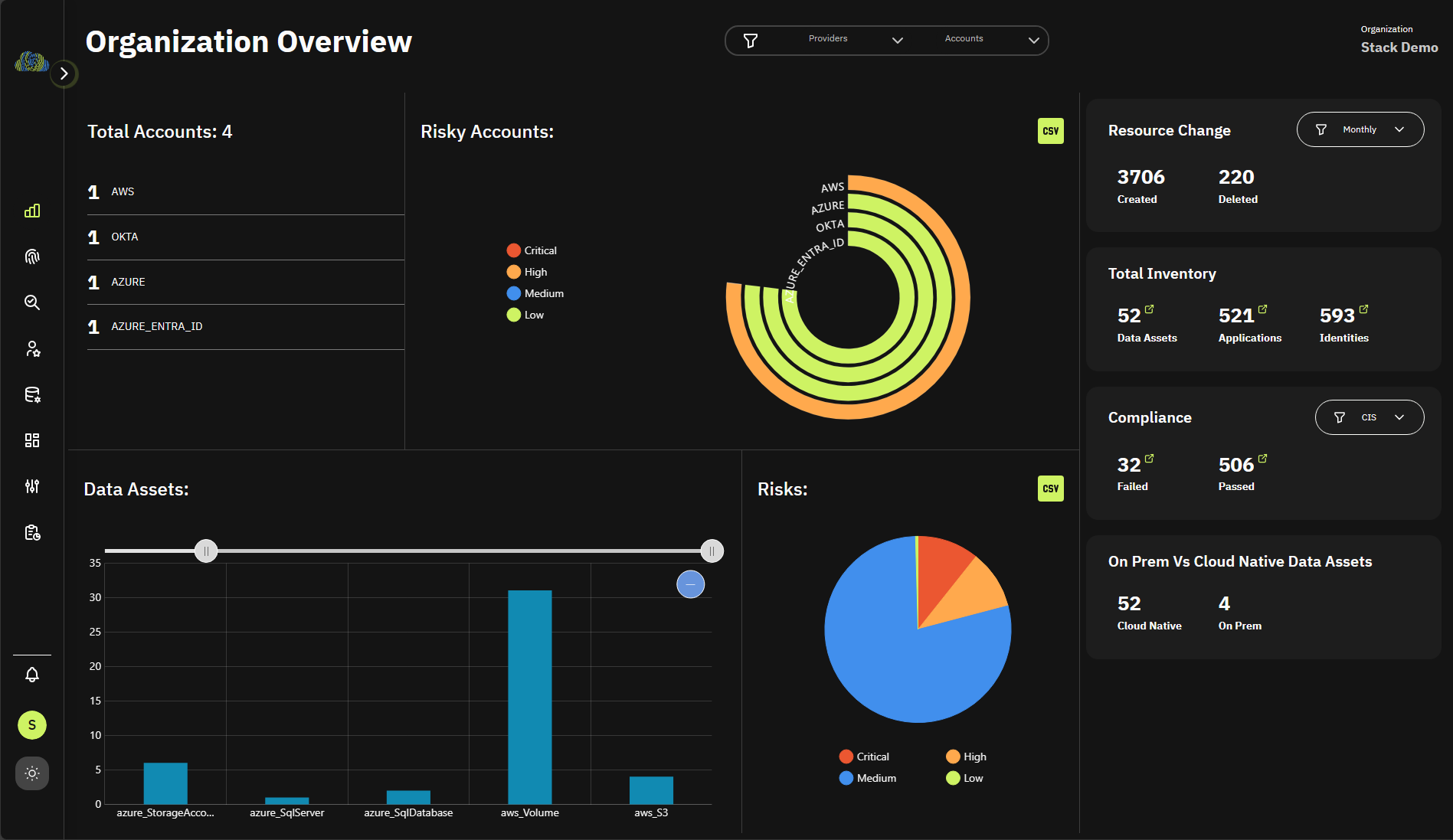
Organization level visibility of your cloud
For easy SOC2 and cloud compliance reports
- Find your identities and roles
- Find your data assets
- Find your cloud infrastructure
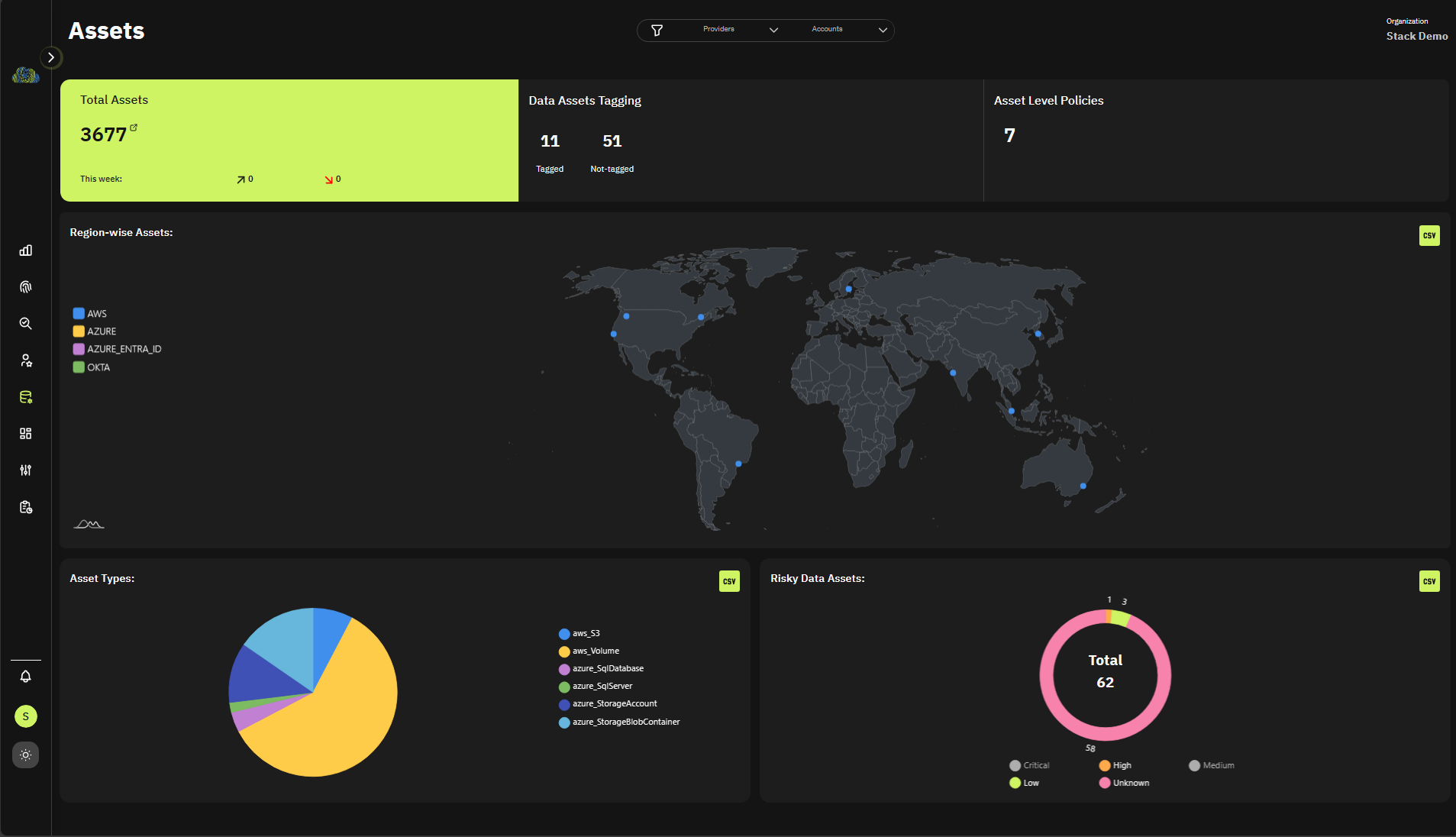
Data Asset Visibility
- See which apps are being used
- See which resources are being used
- See what data is being accessed
- See active identities and permissions
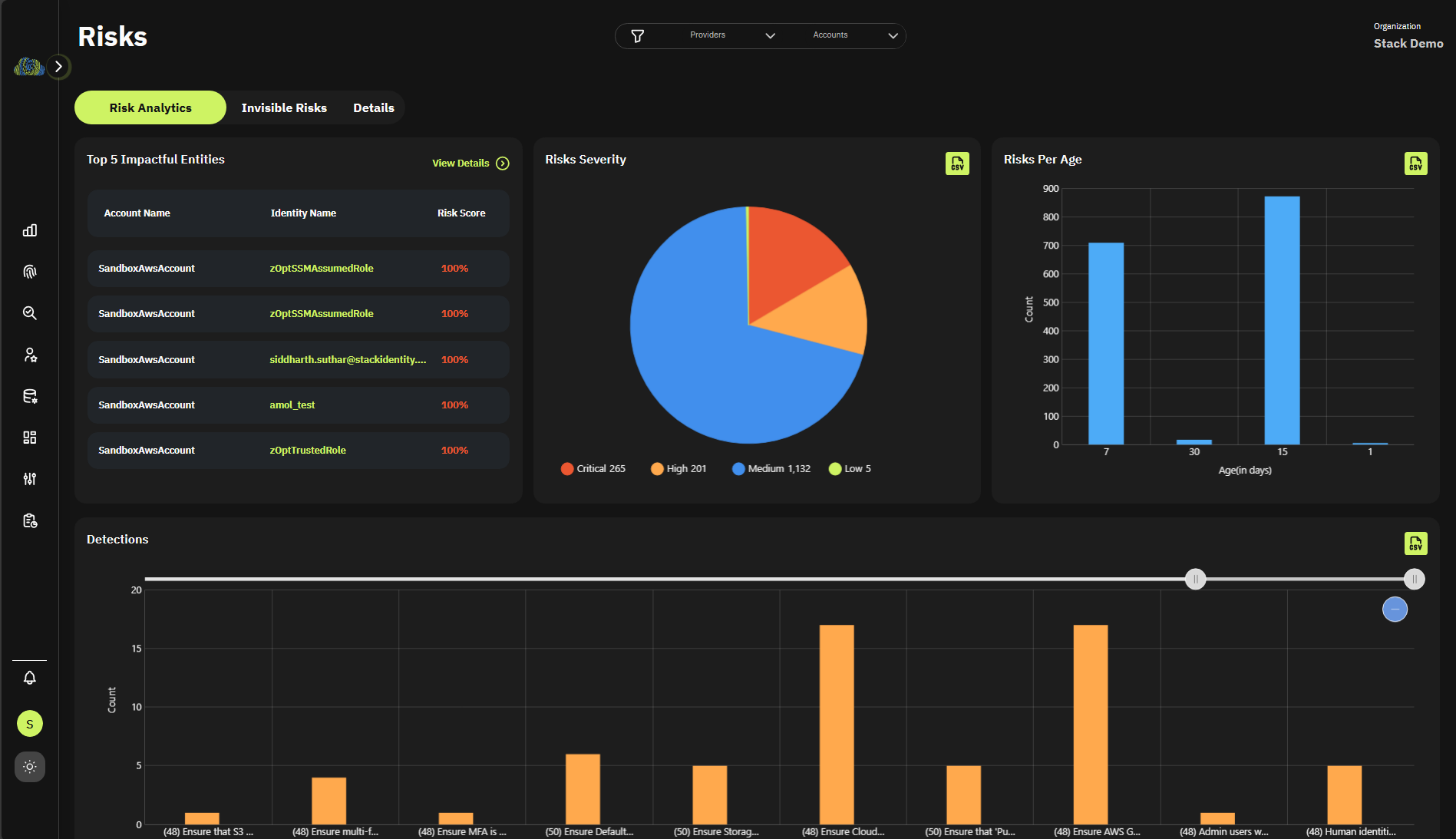
Uncover Vulnerabilities from Exploitable Access
- What application risks exist?
- What data risks exist?
- Who are risky access identities?
- What are risky roles?
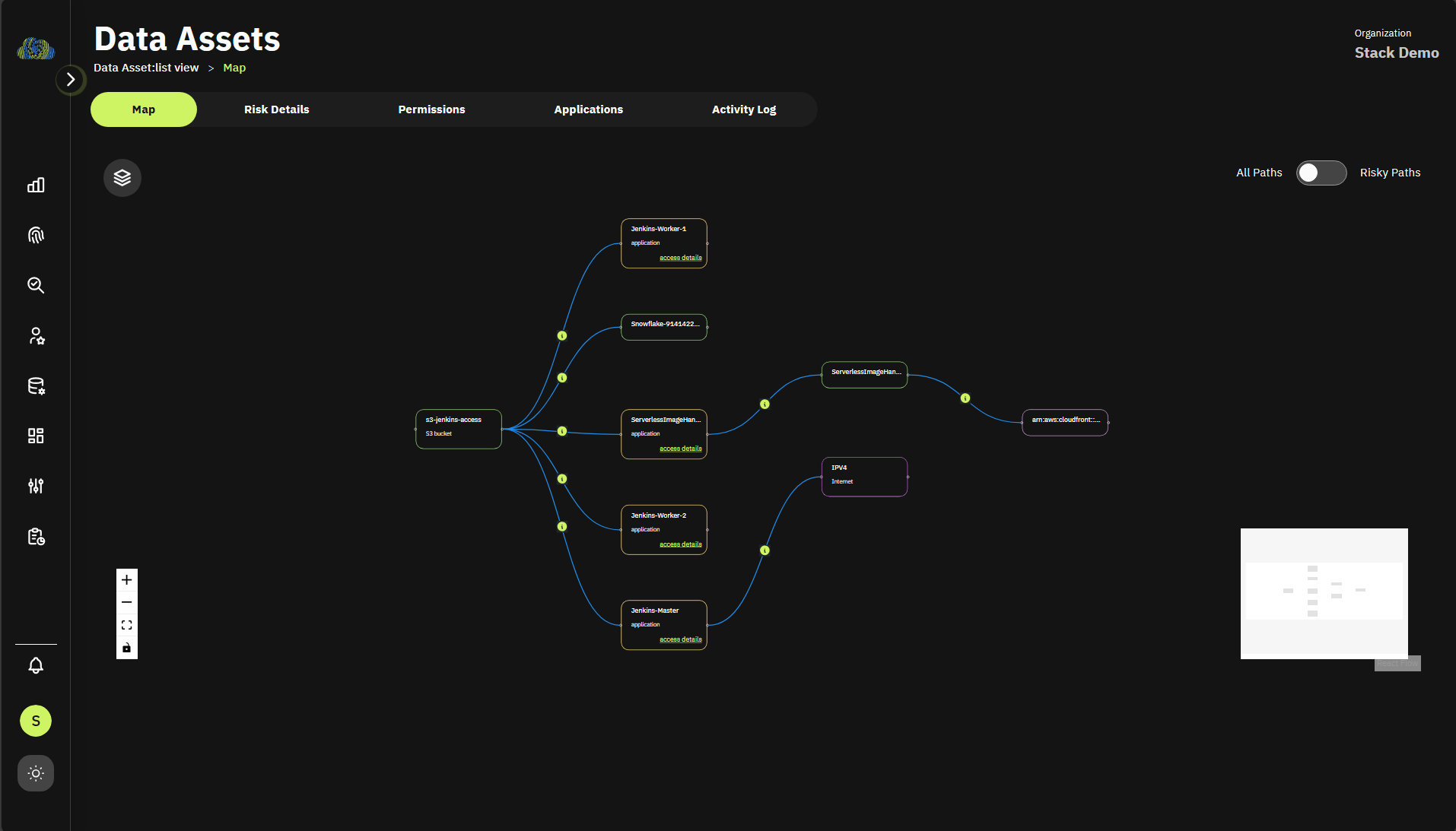
Prioritize and Remediate
- Identify the most exploitable access paths
- Which exposed EC2 instances are at the highest risk?
Due to:- Pathways to sensitive data
- Frequency of access
- External exposure
- Over-provisioned access
- Action risky access and permissions quickly
Ready to see Stack Identity in action?
We’ve said enough. It’s time to see for yourself.