The Shadow Access Impact Report
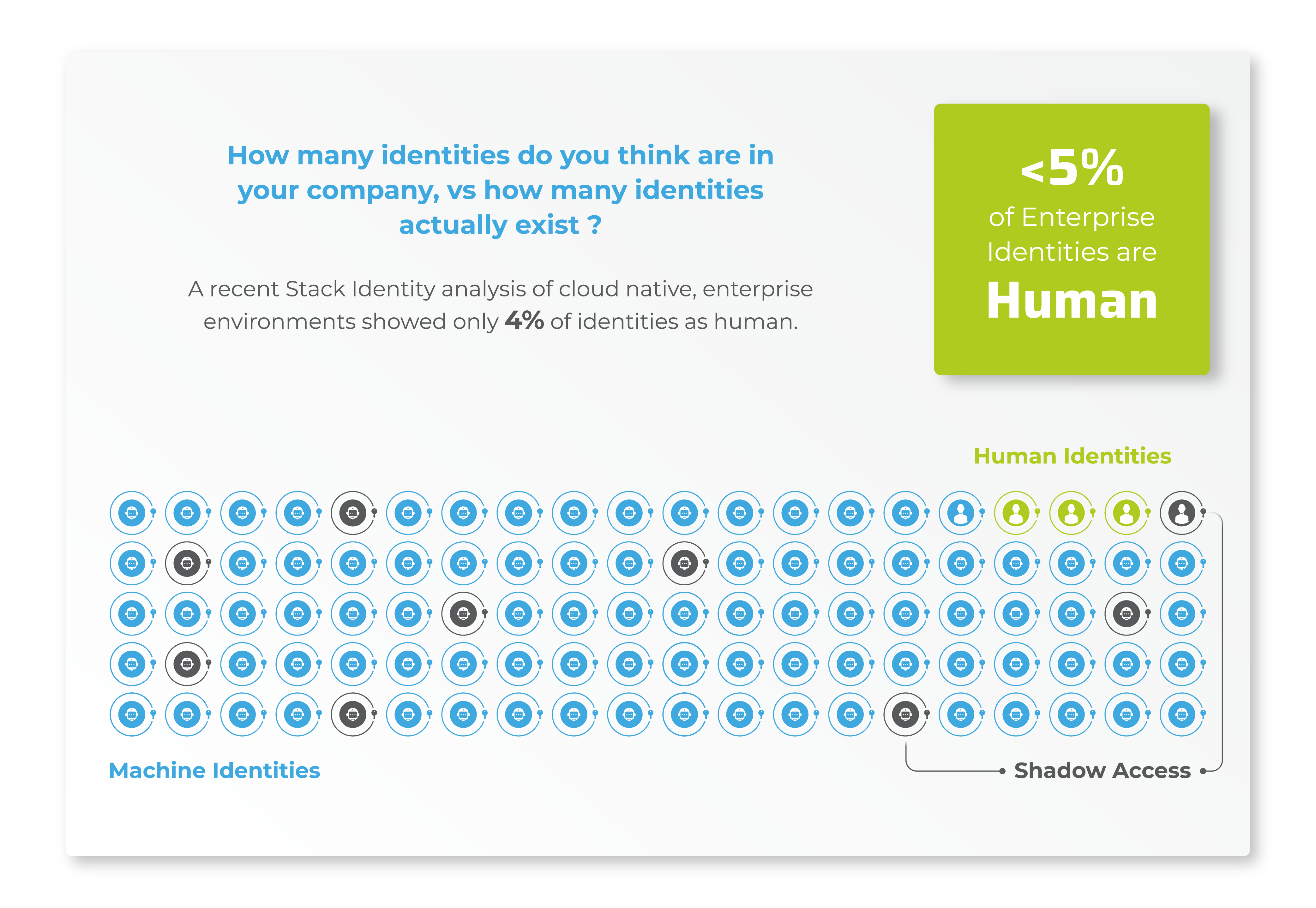
Did you know 80% of breaches are identity related and less than 5% of enterprise identities are human?
Rapid expansion of cloud data, applications, and identities disrupt identity and access management, increasing the risk of cloud and data breaches. Organizations must implement robust security measures to protect sensitive data and mitigate threats. Learn:
- Why the cloud access attack surface is ever expanding
- How toxic combinations of identity and access can be utilized by cyber-attackers to exploit cloud services and data
- About the different access vectors Stack Identity uncovered in live enterprise cloud environments
Download the report to learn how cloud identity and access is disrupting cloud operations, security, and governance. Get ahead and be able to follow an attacker’s traceable cloud IAM footprints.